Identity Management
Identity & Assets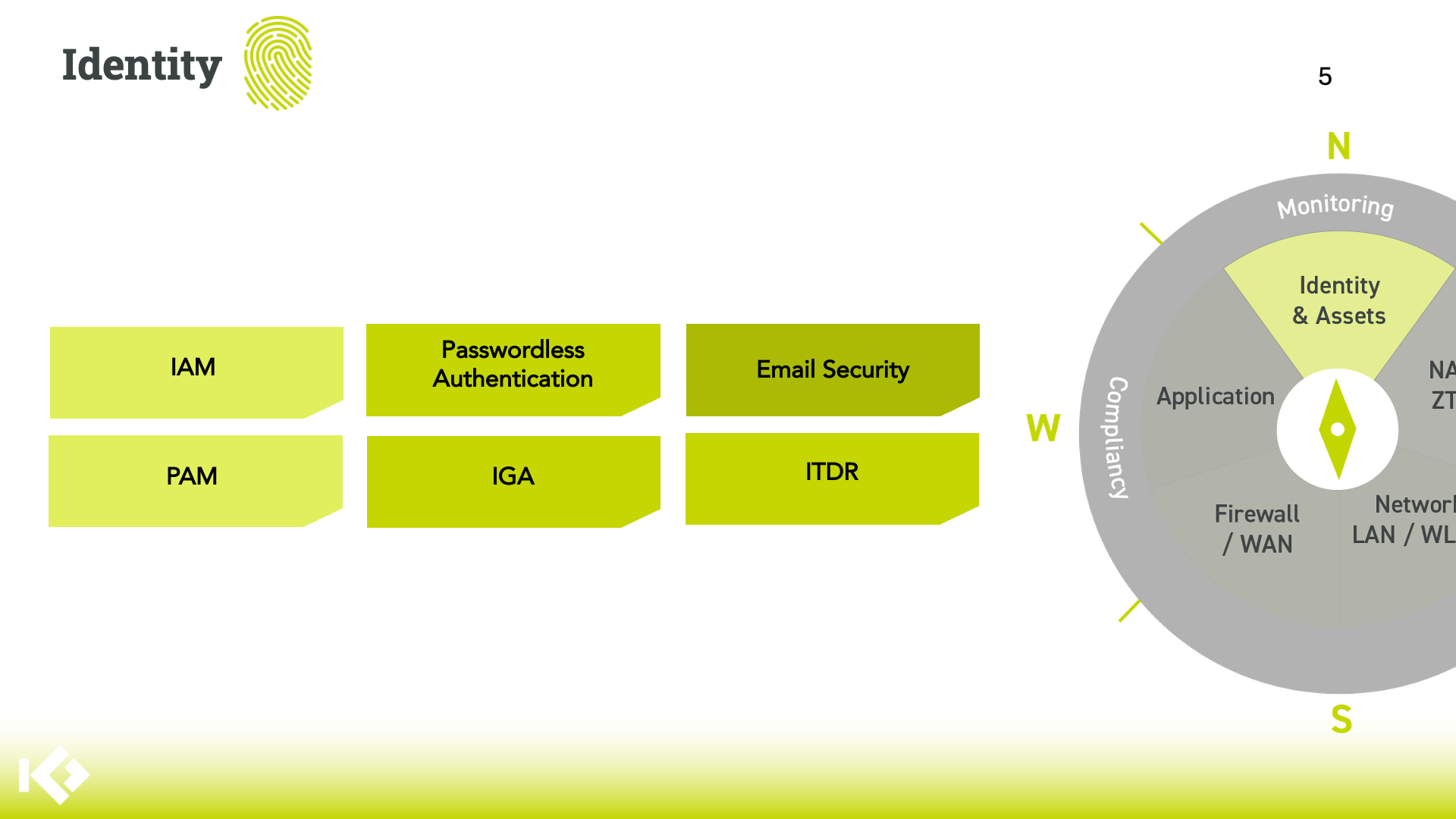
Identity Management Categories
Our Identity portfolio covers six essential areas:
🔑 IAM (Identity & Access Management)
A cybersecurity framework that controls who can access what resources within an organization. It ensures secure authentication and authorization for users, devices and applications. IAM systems handle identity verification through methods like multi-factor authentication (MFA) and single sign-on (SSO), then enforce access based on roles, policies, and least privilege principles. These components manage user lifecycles, from onboarding to deprovisioning, while generating audit logs for compliance.
Featured Solutions: JumpCloud • OneLogin
🔐 Passwordless Authentication
Replaces traditional passwords with more secure, user-friendly methods like biometrics, hardware tokens, or one-time codes to verify identity. It leverages possession or inherence factors, reducing risks from password breaches while streamlining logins. Users enter an identifier like an email address, then prove identity via a device-stored private key unlocked by fingerprint or PIN. The server challenges the device, which signs a response using public-key cryptography without transmitting secrets, ensuring phishing resistance. Passwordless authentication uses standards like FIDO2, an open standard from the FIDO Alliance combining WebAuthn and CTAP for passwordless logins across platforms using hardware authenticators like Onespan).
Featured Solutions: JumpCloud • OneSpan
📧 Email Security
Use layered protection against phishing, malware and business email compromise through cloud-based email gateways such as Barracuda Email Gateway Defense. This gateway scans inbound/outbound email with AI-driven spam filtering, sandboxing for zero-day threats, URL/link protection and DLP to block sensitive data leaks. You can also use post-delivery remediation by searching inboxes for malicious emails via sender/subject, then deleting threats, alerting users, and revoking compromised accounts.
Featured Solutions: Barracuda Networks • Sophos
🛡️ PAM (Privileged Access Management)
Secures elevated accounts like admin or root that control critical systems, enforcing least privilege to prevent misuse by insiders or attackers. It combines credential vaults, session monitoring, and just-in-time access within IAM frameworks
Featured Solutions: JumpCloud • One Identity
👥 IGA (Identity Governance & Administration)
Manages user identities and access rights across hybrid environments, automating provisioning/deprovisioning while enforcing policies for compliance and least privilege. It provides visibility into entitlements, roles and risks, integrating with IAM and PAM to govern the full identity lifecycle.
Featured Solutions: One Identity
🔍 ITDR (Identity Threat Detection & Response)
Detects and responds to identity-based threats like compromised credentials, lateral movement, and anomalous logins in real-time across IAM, IGA and PAM ecosystems. It uses AI-driven behavioral analytics and risk scoring to hunt threats invisible to traditional EDR/XDR systems.
Featured Solutions: Barracuda Networks • Sophos
Best Practices
- Implement Zero Trust - Never trust, always verify. Conditional access can help you with this.
- Enable MFA Everywhere - Add layers of authentication
- Monitor Privileged Access - Watch high-value accounts closely
- Regular Access Reviews - Ensure users have appropriate access
- Automate Onboarding/Offboarding - Reduce human error
Integration with Other Layers
Identity management integrates with:
- NAC/ZTNA - Identity-based network access decisions
- Application - Single sign-on to business applications
- Compliancy - User activity and behavior analytics. Enforce least-privilege
Next Steps: Explore specific identity solutions in the subcategories, or continue to Assets to learn about asset management and endpoint security.