Barracuda ITDR
Overview

Barracuda's approach to identity threat detection and response differs fundamentally from point-solution ITDR vendors. Rather than positioning ITDR as a standalone module, Barracuda integrates identity threat detection as a critical component within a unified platform strategy called BarracudaONE, launched in 2025. Identity threats are addressed through the convergence of three interconnected products: Barracuda Email Security (credential harvest prevention), Barracuda Managed XDR's Cloud Security module (compromised account detection), and the orchestration layer (BarracudaONE) that correlates signals across email, network, endpoint and cloud.
This architectural difference is important: Barracuda doesn't seperate "email" from "identity" from "XDR". Instead, the vendor positions identity threat detection as intrinsic to how modern attacks actually work. A credential theft attack begins with phishing email (harvesting credentials), progresses to compromised account usage (anomalous access patterns, privilege escalation), escalates to lateral movement (multiple accounts compromised), and culminates in ransomware deployment or data exfiltration. By integrating email security with cloud account anomaly detection and endpoint/network visibility within a single platform, Barracuda detects and responds to the entire attack chain, not just the identity component.
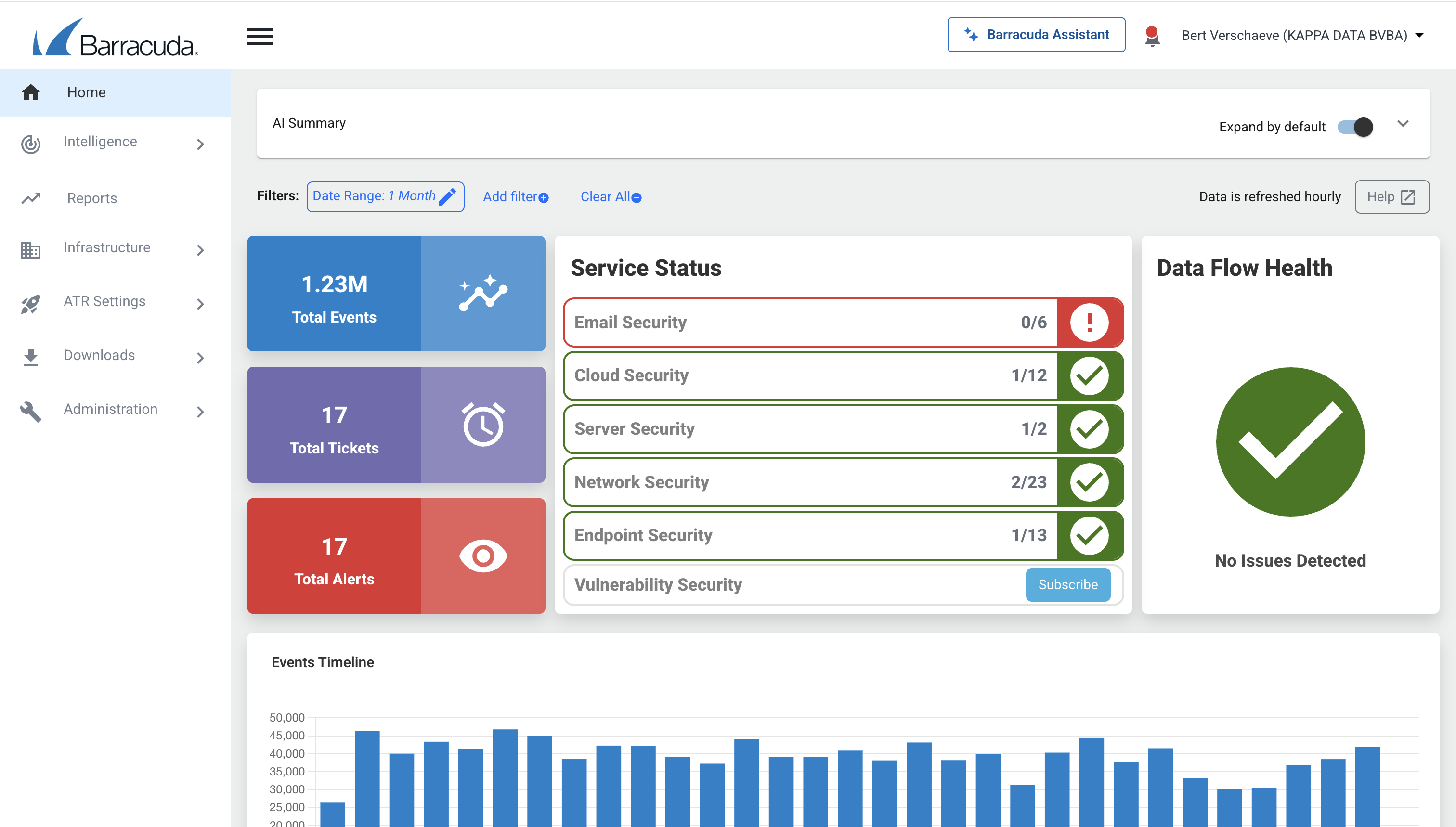
Barracuda Managed XDR, the operational engine for this strategy, operates 24/7 Security Operations Center staffed with Barracuda's own security analysts who investigate alerts, execute remediation, and coordinate cross-layer response. The service is available for endpoint, email, cloud, network and server environments, with Automated Threat Response (ATR) capabilities expanding monthly (September 2025 added Microsoft Defender for Endpoint integration; Google Workspace integration added same cycle).
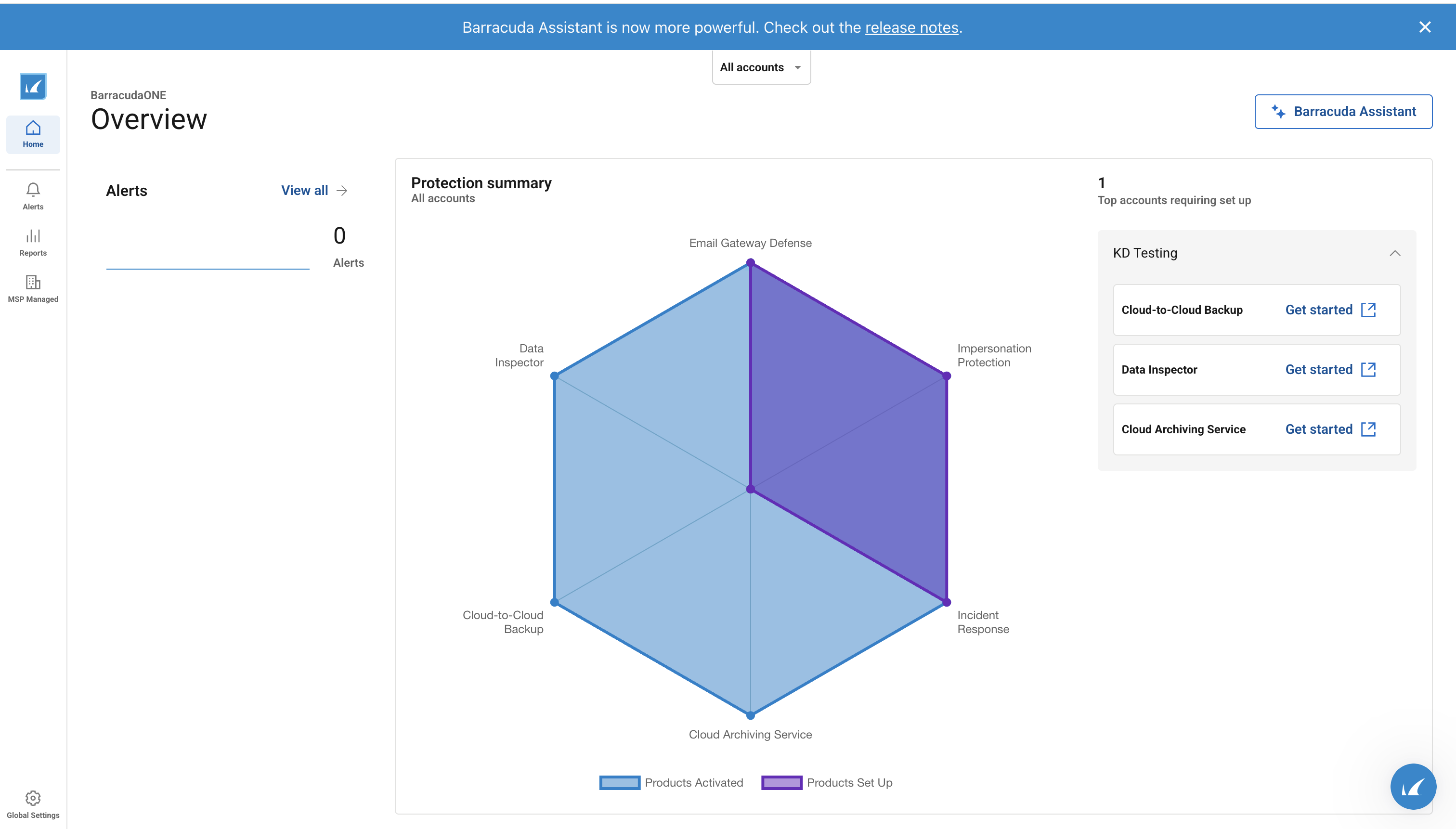
BarracudaONE, the unified platform launched mid-2025, consolidates all these products into a single dashboard with AI-powered correlation, incident ase generation, and the Barracuda Assistant (generative AI copilot) providing real-time guidance during incident investigation and response
How to position?
Organizations already using Barracuda Email Security
This is the highest-probability target segment. Barracuda Email Security protects email with advanced threat detection and is deployed across 600.000+ organizations globally. These customers already understand that email is the attack vector and have budgeted for email security
However, these email security customers have a critical blindspot: once attackers compromise an employee account (by stealing credentials through phishing), Barracude Email Security stops monitoring that account. The attack continues inside, compromised accounts are used to send phishing emails to other employees, access sensitive data, pivot to other systems, and establish persistence. Traditional email security can't detect this because it sees legitimate logins from the compromised account.
Barracuda Manged XDR with Cloud Security module specifially addresses this gap. When combined with Email Security, it creates end-to-end protection of the credential attack chain: Email security prevents harvest; XDR detects abuse.
Microsoft 365-Dependent Organizations
Organizations running Microsoft 365 for email and collaboration use Barracuda Email Security as gateway defense and often Barracuda Managed XDR for cloud threat detection. However, Microsoft's native email security (Microsoft Defender for Office 365) is common in this segment as well.
Barracuda has a compelling differentiator here: Barracuda Email Security detects 47% of threats that Microsoft 365's native email security missed. This isn't hypothetical, it's documented across customer deployments. The threats Microsoft misses are precisely the identity-based attacks: advanced BEC, conversation hijacking, account takeover precursors.
When Barracuda Email Security detects a phishing email attempting to harvest Microsoft 365 credentials, it can integrate with Barracuda Managed XDR's Cloud Security module to:
- Detect if the credentials were actually compromised
- Monitor that account for anomalous behavior,
- Automatically disable the account if suspicious activity is detected.
Managed Service Providers & Resellers
Barracuda explicitly targets MSPs with BarraucdaONE. The unified platform enables MSPs to manage thousands of customer environments through a single console, automatically correlate threats across customers, and leverage Barracuda's 24/7 SOC as a managed service offering rather than requiring the MSP to staff SOC expertise
MSPs are high-value because they:
- Manage multiple customer environments and generate recurring revenue per deployment
- Have inherent scalability (adding customers doesn't require architectural changes)
- Are frustrated with tool proliferation and unified platform adoption
- Benefit from the economics of shared SOC teams provided by Barracuda
An MSP managing 500 customer environments can use BarracudaONE to:
- Identify which customers have exposed credentials (Email Security detects phishing --> credentials compromised --> Cloud security detects anomalous account usage)
- See which environments have misconfigurations enabling credential compromise (security posture gaps)
- Automatically remediate threats across all customers without per-environment manual response
Core Features
Barracuda Email Security
Barracuda Email Security is the foundational layer protecting against credential theft attacks.
Core Capabilities:
Advanced Threat Protection (ATP):
- Detects phishing emails with sophisticated impersonation and payload evasion
- Multimodal AI analyzes visual content (renders PDFs, detects malicious QR codes)
- Zero-day attack detection through sandbox analysis
- Attachment and link rewriting with real-time scanning
Business Email Compromise (BEC) detection:
- BED-Guard ML model achieves 98.2% precision with less than 1 false positive per 5 million emails
- Detects spear phishing, CEO fraud, wire fraud requests, credential-harvesting emails
- Maps internal social networks to understand normal communication patterns and detect deviations
- Detects conversation hijacking (compromised account used to continue legitimate conversation thread with fraud request)
Impersonation Protection
- Maps organizational structure to detect when externally-spoofed addresses masquerade as company executives or domain
- Detects lookalike domains and variations
- High-risk employee analysis identifies individuals targeted and alerts IT
Account Takeover Detection (Post-Phishing)
- Real-time defense when account is actually compromised (phishing succesful, credentials stolen/used)
- Detects anomalous email patterns from compromised account (unusual recipients, unusual send times, unusual volumes)
- Alerts IT and external users; automatically quarantines outgoing phishing emails sent from compromised account
- Blocks attacker access and provides visibility into inbox rule changes indicating attacker persistence
Barracuda Managed XDR: Cloud Security Module (Credential Abuse Detection)
When credentials are stolen but the Email Security didn't prevent the phishing (or external breach exposed credentials), Barracuda Managed XDR's Cloud Security module detects and responds to commpromised account usage
Cloud Account Anomally Detection
- Monitors Microsoft 365, Azure, Google Workspace, Okta, AWS CloudTrail, Duo for suspicious account activity
- Detects account takeover attempts: anomalous logins, impossible travel, unusual geographic locations, unusual devices
- Detects MFA fatigue attacks (attackers requesting MFA approvals until user approves or device is stolen)
- Detects suspicious admin activity: unauthorized admin changes, policy modifications, delegation of authority
Specific Identity Threat Detection
- Impossible logins: Logins from geographically impossible locations (Brussels then Tokyo within 5 minutes)
- Account takeover indicators: Multiple failed logins followed by succesful access; access from known threat actor IP; unusual bulk operations (mass email forwarding, large file downloads)
- Privilege escalation: Elevation of non-privileged accounts to admin; creation of new admin accounts; modification of security settings
- Insider threat patterns: Bulk sensitive data access before departure; access to systems unrelated to role; unusual file sharing with external addresses
- MFA fatigue: Repeated MFA approval requests; disabled MFA on accounts; MFA device changes
Email-Cloud Correlation
- When Email Security detects phishing email targeting a Microft 365 account, it automatically tags that account for enhanced monitoring in Cloud SecurityIf he recipient actually clicked the phishing link and entered credentials, Cloud Security detects the account takeover automatically and alerts the SOC team
- Example: Phishing email detected --> Email Security quarantines --> But one employee already fell victim --> Cloud Security detects impossible travel login from attacker's location --> ATR automatically disables account wihin seconds
Barracuda Managed XDR: Automated Threat Response (ATR)
When identity threats are detected, Barraucda Managed XDR can automatically execute response actions without human intervention. As of September 2025, ATR is available for:
Microsoft 365 Cloud Security ATR
- Disable compromised user account
- Logout all active sessions
- Disable MFA temporarily (forcing re-registration)
- Alert SOC team and customer IT Microsoft Defendor for Ednpint ATR (New Sep 2025)
- Isolate infected device from network
- Send high-severity alert
- Trigger phone call from Barracuda SOC within seconds
- Restore connectivity when threat is cleared Google Workspace ATR (New Sep 2025)
- Logout commpromised user from all sessions
- Disable account
- Alert SOC and customer Firewall ATR
- Automatically block IP addresses with poor reputation
- Block command-and-control connections in real-time
- Block data exfiltration attempts Azure/SentinelOne ATR
- Endpoint isolation
- Process termination
- Network restriction
Barracuda's roadmap explicitly includes expanding ATR to additional platforms monthly
BarracudaONE Platform Integration
BarracudaONE is the orchestration and correlation layer enabling identity threats detected across email, cloud, endpoint and network to be unified, prioritized and responded to as a single incident.
Consolidation Alert Feed
- Aggregates alerts from Barracuda Email Security, Cloud Security, Network Security, Endpoint Security
- Eliminates alert fatigue through intelligent correlation (8 low-confidence alerts correlated into 1 high-confidence incident)
- Unified triage workflow lets security teams prioritize by actual risk, not by tool
Automatic Case Generation
- When correlated threats meet incident criteria, BarracudaONE automatically creates an investigation case with full context
- Case includes: alert timeline, affected users/systems, observed attacker behaviors, recommended response actions
- SOC team receives richly contextualized case rather than isolated alerts
Barracuda Assistant (AI Copilot)
- Generative AI integrated into BarracudaONE dashboard
- Provides real-time guidance during incident response
- Answers natural language queries
Deployment Health & Posture Management
- Identifies which Barracuda products are deployed in which customer environments
- Flags misconfigured tools (MFA disabled, policies not enforced, weak settings)
- Provides configurations recommendations
- Helps MSPs ensure all customer environments have consistent, hardened settings
24/7 Managed Security Operations Center (SOC)
The differentiator is the human element. Barracuda Managed XDR includes 24/7 analayst coverage where Barracuda's SOC team investigates alerts, makes escalation decisions, and executes remediation.
When a threat is detected (eg impossible travel login + new admin account creation + mass email forwarding), the SOC analyst receives the case and:
- Investigates correlation with other evidence
- Determines if threat is genuine or false positive
- Decides remediation scope and timing
- Executes response (disable account, isolate endpoint, revoke sessions)
- Documents incident with forensic details for customer's compliance records
For small organizations without security staffing, this means identity threat detection and response capability equivalent to hiring a security analyst, but distribued across Barracuda's shared SOC team (reducing cost and providing 24/7 coverage)
Feature Overview
Email Security + XDR Integration architecture
The architectural key to understanding Barracuda's ITDR approach is how Email Security and XDR work together as credential attack lifecycle defense
Stage 1: Phishing Prevention (Email Security)
- Attacker sends credential-harvesting phishing email
- Barracuda Email Security multimodal AI detects phishing
- Email is quarantined; user never sees it
- Outcome: Credential theft prevented
Stage 2: Attempt to Compromise Account (Email Security + Cloud Security)
- If phishing Email is missed (or external breach exposed credentials), attacker tries login
- Email Security detects account takeover attempt in real-time: unusual login patterns, impossible travel, MFA manipulation
- Cloud Security (in XDR) correlates: Is this login associated with a phishing email we detected? Is it from a known threat actor IP? Is it from impossible location?
- Outcome: Account takeover detected; user alerted
Stage 3: Weaponize Compromised Account (XDR Cloud Security)
- If account is compromised, attacker uses it to send phishing to other employees, access data, move laterally
- XDR Cloud Security detects: new inbox forwarding rules (attacker hiding phishing responses), unusual email sends, delegation of authority, access to sensitive systems
- Outcome: Compromise amplification detected
Stage 4: Response & Containment (ATR)
- ATR automatically disables compromised account
- If Microsoft Defender for Endpoint (or managed SentinelOne agent) is in use, Barracuda also isolates endpoint where login originated
- If Google Workspace, Barracuda logs out all sessions
- SOC analyst investigates scope: Were other accounts compromised? Is this part of targeted campaign? Should additional customers be checked?
- Outcome: Attack contained in minutes instead of hours/days
Conclusion
Barracuda's ITDR approach is fundamentally different from point-solution competitors. Rather than positioning ITDR as a specialist product, Barracuda positions identity threat detection as intrinsic to how attacks actually work: attacks begin with email (credential theft), continue through compromised cloud accounts, and exploit multiple systems for persistence and data exfiltration.
By integrating email security, cloud threat detection, endpoint detection, and network detection within a unified platform (BarracudaONE), Barracuda detects and responds to identity threats as part of the entire attack chain rather than in isolation
Why is this positioning powerful?
-
Platform Consolidation Resonates with Tool-Fatigued Organizations A 2025 global survey found 65% of IT Professionals report managing too many security tools, making tool sprawl a universal pain point. Barracuda's consolidation angle is compelling: one platform, unified dashboard, coordinated response, less training required. For organizations already using fragmented tools, BarracudaONE represents operational relief
-
Email Security Differentation is Quantified "Barracuda detects 47% of threats Microsoft 365 misses" is a concrete, defensible advantage. Organizations can immediately validate this by deploying Barracuda Email Security alongside their Office 365 email platform and see what Barracuda catches that Microsoft doesn't.
-
Managed XDR Addresses SOC Resource Gap Most midmarket and SMB organizations lack security staffing for 24/7 operations. Barracuda Managed XDR elminates the need to hire SOC analysts. Barracuda's shared SOC team investigates threats and executes response on the customer's behalf. This is economically compelling for small security teams managing complex environments
-
Multi-Cloud Reality is Addressed Organizations using Microsoft 365, Google Workspace, AWS, Okta together face fragmented identity security. Barracuda Managed XDR monitors all of these within a single platform with coordinated response