Sophos ITDR

Overview
Sophos Identity Threat Detection and Response (ITDR) launched in October 2025 as fully integrated add-on to Sophos XDR and Sophos MDR, built on the proven Secureworks Taegis IDR platform acquired by Sophos. Unlike point solutions requiring separate deployment, Sophos ITDR is architected as a native component of Sophos Central, the unified security platform, ensuring seamless integration with endpoint detection and response (EDR), managed detection and response (MDR), and extended detection and response (XDR) capabilities
The product addresses a market gap with precise timing. Identity-based attacks now drive 86% of breaches, with stolen credentials appearing on dark web markets within minutes of compromise. Yet traditional identity security tools (IAM, SIEM) operate as separate silos, leaving identity threat detection to generic rule-based alerts that generate excessive false positives (as documented in Microsoft ITDR failures). Sophos ITDR bridges this gap by delivering identity-specific threat detection, behavioral analytics, and dark web intelligence consoldiated within a single operational interface.
Sophos ITDR is currently available in Sophos Central. It operates as software monitoring (not a managed service itself), but when combined with Sophos MDR, provides managed identity threat response where Sophos analysts investigage and execute remediation actions 24/7
The product represents Sophos' fist major launch following its October 2024 acquisition of Secureworks (Taegis), bringing enterprise-grade identity threat detection heritage directly into the Sophos ecosystem. This creates significant competitive advantage: Sophos ITDR combines Secureworks' dark web intelligence (Secureworks Threat Team operates one of the world's largest dark web monitoring operations), Sophos's 600.000 customer endpoint detection infrastructure, and MDR capabilities serving customers globally
How to position
Financial Services & Banking
Financial insitutions represent the highest-value, highest-urgency target for Sophos ITDR. These organizations face converging pressures: DORA compliance requires "advanced authentication" and "continuous monitoring" of identity threats with mandatory incident response capabilities. Customer testimonials directly from financial services CISOs describe Sophos ITDR as "a game changer for strenthening overall security posture" by providing centralized identity risk visibility previously absent. (https://finance.yahoo.com/news/sophos-launches-itdr-protect-against-100000540.html)
Healthcare
Healthcare organizations face identical compliance pressures. Additionally, healthcare operates on tight margins with limited security staff, making the Sophos MDR integration valuable. Sophos has positioned specifically for healthcare with dedicated MDR offerings addressing patient data protection, connected medical device security, and clinical system protection. ITDR naturally extends this existing relationship.
Government & Critical Infrastructure
Government agencies designated as critical infrastructure under NIS2 face mandatory identity monitoring requirements. Critical infrastructure operators must meet NIS2 requirements with specific technical controls including "advanced authentication", "continuous monitoring" and "incident detection and resposne" capabilities.
Government and critical infrastructure budgets are large and compliance-driven. They operate complex hybrid environments that create identity visibility gaps. Threat actors specifically target these sectors for espionage and operational disruption, making credential-based attacks a tactical focus.
Midmarket Enterprises
Midmarket organizations use Sophos endpoint security, often operate Entra ID without comprehensive ITDR, and typically have 2-5 person security teams. This segment has budget constraints but also has significant compliance pressures (many are NIS2-mandated.) They're frustrated with Microsoft's ITDR false positives and dark web intelligence gaps.
The midmarket segment is highest-probability for rapid ITDR adoption because:
- Sophos already has endpoint relationships
- ITDR is positioned as an add-on, not a disruptive replacement
- MDR integration means small security teams don't need to staff identity expertise
- Pricing is typically consumable within existing security budgets
Cross-Sell Opportunities
Sophos MDR customers already trust Sophos with 24/7 threat detection and response. ITDR is a natural expansion of this relationship. It extends MDR's scope from endpoint, network and email to identity. The integration is seamless: identity threats automatically generate MDR cases, enabling analyst driven response.
Organizations running Sophos endpoint and Sophos email protection often lack comprehensive threat detection services. ITDR + XDR bundling creates an attractive upgrade path.
- Sophos ITDR is positioned as the specialist solution that does Entra ID identity monitoring correctly. It eliminates false positives through behavioral analytics and provides dark web monitoring Microsoft lacks
- Organizations currently in compliance readiness assessments for NIS2 or DORA identified identity monitoring as a compliance gap and are actively purchasing. These organizations have dedicated compliance budgets and are following architectural guidance from auditors/consultants
Core Features
Identity Catalog & Full Visibility
Sophos ITDR begins with comprehensive identity inventory across all systems and identity sources: on-premises Active Directory, cloud identity providers (Microsoft Entra ID, Okta, Ping Identity, Google Workspace), SaaS applications, service accounts, API keys and OAuth tokens. The Identity Catalog provides a consolidated view eliminating blind spots where identities exist but lack monitoring
This foundational capability is critical because most organizations are surprised by their actual identity inventory. Dormant accounts remain active (employees who left months ago), service accounts proliferate without governance (applications create accounts for automated tasks), OAuth integrations accumulate unseen (hundereds of third-party apps requesting access), and privileged accounts escape oversight (multiple administrators, legacy system owners).
The Identity Catalog surfaces this inventory in a prioritized dashboard, enabling security teams to immediately identify high-risk identities and misconfigurations without manual discovery processes.
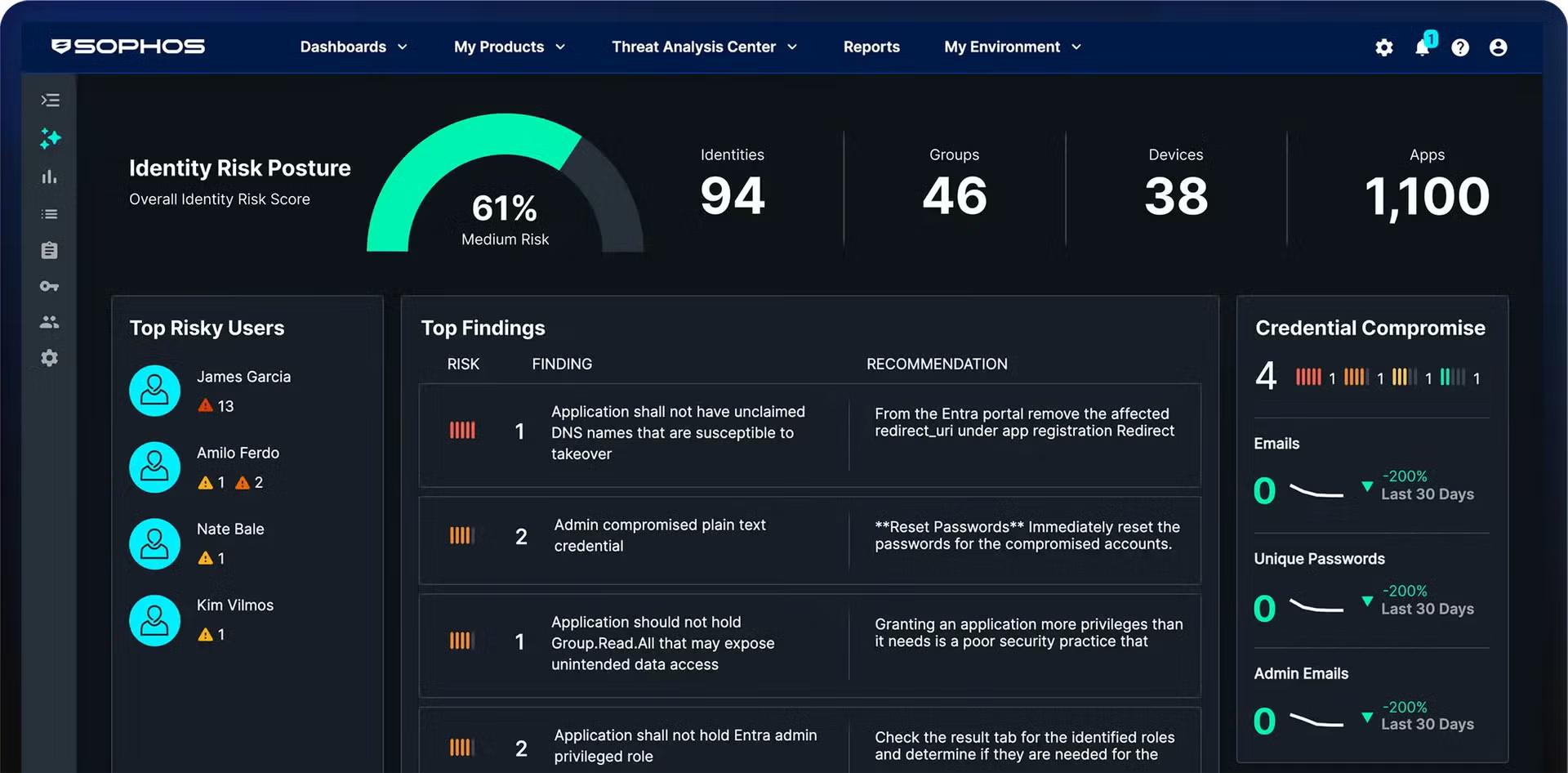
Identity Risk Posture Dashboard
The IDentity Posture Dashboard provides a single, prioritized view of all identity risks discovered across the environment. This includes:
- Compromised credentials detected on dark web (active, real-time alerts when stolen credentials surface)
- Configuration Misconfigurations (overly permissive access, disabled MFA, legacy authentication protocols)
- Dormant or orphaned accounts (accounts with standing access but no recent activity)
- Risk-based prioritization (highest-risk findings surfaced first based on impact and exploitability)
- Identity Risk Posture score (benchmark metric showing organization's identity security posture over time, enabling ROI measurement)
The dashboard updates dynamically. Entra ID posture checks run every 2 hours; dormant resource checks run every 2 hours; Identity Risk Posture score updates daily. This ensures discovery of newly introduced risks (new permissions granted, new OAuth applications, policy changes) within a detection window measured in hours, not days
This solves the operational problem of identity risk overwhelm: security teams no longer manually audit identity configurations or search dark web marketplaces. Sophos ITDR continuously performs these tasks and prioritizes findings by risk
Continuous Posture Assessments
Sophos ITDR performs more than 80 automated cloud identity posture checks, going far beyond basic hygiene like "is MFA enabled?" These checks include
- Authentication configuration: Legacy authentication protocol usage (Basic Auth disabled?), password complexity enforcement, authentication method inventory
- MFA coverage and gaps: Conditional access policies, MFA enforcement for privileged accounts, device compliance requirements
- Access permissions: Privilege creep (users with standing elevated access who don't need it), permission consistency (similar users with significantly different permissions), role-based access implementation
- Account lifecycle management: Dormant accounts (inactive > 30 days, > 90 days), orphaned accounts (created but never used), accounts post-employee departure
- Vulnerability detection: Unpatched identity systems, legacy identity infrastructure, kwnown vulnerable configurations
- Data protection: Sensitive data acess patterns, encryption enforcement, DLP integration readiness
Each check is risk-scored. A dormant administrator account has higher risk than an inactive contractor account. An application with excessively broad permissions scores higher than one with scoped access. This risk-based prioritization prevents alert fatigue by surfacing only findings that matter
Organizations typically discover 40-60 critical or high-risk findings wihtin the first assessment, often uncovering years of accumulated configuration drift
Dark Web Credential Intelligence
Sophos ITDR includes native dark web monitoring sourced from Secureworks' global threat intelligence infrastructure. Secureworks' Threat Intelligence team operates one of the world's largest dark web monitoring operations, scanning underground markets, threat actof rosum, paste sites, and breach databases in real-time
When employee credentials appear in stolen credential listings, Sophos ITDR immediately alerts the customer with:
- Credential details: Which user's credentials were exposed, which service (email, domain password, SaaS application)
- Breach source: Which dark web marketplace or forum the credentials appeared in
- Exposure type: Were credentials plaintext, hashed or salted? Are they dated or current?
- Correlated findings: Are other credentials from the organization already circulating?
- Automated response: (If MDR integrated) Immediate password reset, session termination, account lock
The speed is critical. Traditional incident response discovers compromised credentials through audit trails after attackers have already exploited them (average 292-day dwell time). Sophos ITDR's dark we monitoring detects credentials before exploitation, enabling prevention rather than response
User and Entity Behavior Analytics (UEBA)
UEBA detets anomalous identity activity indicating account compromise or insider threats. Sophos ITDR uses machine learning to establish behavioral baselines for each identity and detects deviations indicating compromise
Behavioral anomalies detected include:
- Impossible travel: User logs in from geographically impossible locations (Brussels 10AM, Tokyo 11 AM same day)
- Unusual access timing: Access to sensitive systems outside normal working hours or patterns
- Resource access anomalies: User accessing systems unrelated to their role; finance staff accessing engineering repositories; junior employees accessing executive financial reports
- Privilege escalation: Users with standing basic permissions requesting elevated access; service accounts escalating privileges
- Account takeover indicators: Multiple failed logins followed by succesful login from anomalous location; unusual bulk operations (mass email forwarding rules, bulk file download)
- Insider threat patterns: Bulk sensitive data access before known departure; unusual file sharing with external addresses; database query patterns inconsitent with legitimate job function
The behavioral analytics are AI/ML driven, continuously learning from user activity within the organization's context. This reduces false positives relative to static rule-based detection: a CISO loggin in at 2 AM is norma; a junior support technician logging in at 2 AM is suspicious. Sophos ITDR learns these distinctions automatically
Advanced Identity Threat Detection
Sophos ITDR is engineered to detect all known MITRE ATT&CK Credential Access techniques with detection rules covering 100% of known methods. Detection patterns include:
- Kerberoasting: Attackers requesting Kerberos service account tickets offline for cracking; Sophos detects unusual service account ticket requests
- Password spraying/brute force: Distributed authentication attempts across multiple users; Sophos detects unusual authentication failure patterns
- Privilege escalation: Unauthorized attempts to gain elevated access; Sophos detects sudoers, UAC bypass attempts, unusual admin activity
- Lateral movement: Compromised accounts authenticating to new systems uncharacteristically; Sophos detects unusual service-to-service authentication
- Token abuse: OAuth tokens used from unusual locations or with unusual permissions; Sophos detects token refresh anomalies and unexpected token-based API activity
- Session hijacking indicators: Multiple sessions for single user; session activity from unusual locations
- Compromised credential misuse: Stolen credentials used for unauthorized access; Sophos combines dark web intelligence with login anomalies to detect exploitation in progress
Response Automation & Playbooks
When threats are detected, Sophos ITDR enables immediate automated response with no human intervention required, or rapid analyst-driven response (if MDR integrated). Automated resposne actions include:
- Account Lockdown: Lock accounts with suspected compromise, preventing further unauthorized access
- Session Termination: Force logout all active sessions for compromised accounts, revoking attacker access
- Password reset: Force immediate password reset, invalidating attacker's stolen credentials
- MFA refresh: Enforce re-registration of MFA devices, invalidating stolen MFA tokens or recovery codes
- Session revocation: Revoke specific suspicious sessions while maintaining legitimate access
- Account flagging: Mark accounts as compromised in identity system (triggering downstream conditional access policies, device re-enrollment, etc)
These actions occur in seconds, compared to hours of manual incident response. The earlier an account compromise is contained, the less opportunity attackers have to escalate privileged, move laterally, or extract data
Feature overview

Integration with Sophos Central
Sophos ITDR is deployed as a fully native module within Sophos Central, Sophos's unified security platform. This architecture is critical to understanding Sophos ITDR's operational efficiency to point solutions
Sophos Central serves as the hub where:
- Identity telemetry: Entra ID logs, Active Directory audit trails, SaaS application logs flows into a centralized data lake
- Detection engines including ITDR consume this telemetry and generate priority-ranked alerts
- EDR agents such as Sophis Intercept X send endpoint signals that correlate with identity activity
- XDR and MDR services consume the aggregated data to detect cross-layer attack patterns
- Response orchestration (automated or manual) initiates actions across tools
Example: EDR detects suspicious activity on an endpoint --> ITDR checks if the endpoint owner's identity is behaving abnormally --> If correlation exists, a single cross-platform alert is generated with both endpoint and identity context --> MDR analysts receive richly contextualized incident requiring investigation --> Single response ation (disable account + isolate endpoint) addresses both layers
This is fundamentally different from siloed identity solutions that detect threats in isolation without endpoint context
XDR Integration
When Sophos ITDR detects a threat or high-risk finding, it automatically generates a case within Sophos XDR. This case includes:
- Alert context: What was detected (compromised credential, behavioral anomaly, configuration risk)
- Severity level: Risk-based prioritization enabling XDR to queue high-risk cases for rapid analysis
- Correlated telemetry: Endpoint activity from the affected identity's devices (if available), recent login patterns, access history
- Recommended response: Suggested remediation actions ranked by impact
- Compliance mapping: Which regulatory requirement this finding addresses
Sophos XDR then surfaces this case in its threat analysis console, enabling security analysts to investigate with complete context. For organizations running XDR without MDR, this means their internal team gets identity-contextualized threat investigation data they previously lacked
MDR Integration
- Detection: Sophos ITDR detects a threat (e.g. employee credentials on dark web, suspicious privilege escalation)
- Case generation: Alert automatically escalates to Sophos MDR case management
- Analyst investigation: Sophos SOC analyst receives the case with full context (behavioral data, risk scores, recommended actions)
- Analysis & decision: Analyst determines if threat is genuine or false positive; decides on response timing and scope
- Action execution: Analyst forces password reset, locks account, revokes sessions, or coordinates incident response as needed
- Customer notification: Customer receives incident report documenting threat, investigation, and remediation
This dramatically changes the operational economics for small organizations. Instead of hiring a full-time identity security analyst organizations leverage Sophos's shared SOC team. The trade-off is reduced customization, but the ROI is compelling for midmarket organizations.
Dark Web Monitoring Details
Sophos ITDR's dark web intelligence is sourced from Secureworks' Threat Intelligence Team, which operates continuous scanning of:
- Dark web marketplaces: (Russian Market, BrachDB, and emerging alternatives following Law Enforcement shutdowns)
- Threat actor forums (XSS, Exploit, Lolita City, and specialized forums focused on credential trading)
- Paste sites (Pastebin, GitHub, Gist, and specialized paste services)
- Breach Databases (Have I Been Pwned aggregation, Breachforums, specialized databases)
- Leaked password collections (Combined password lists, dictionary attacks, previous breach compilations)
Coverage includes corporate credentials (domain emails, VPN access, admin credentials), SaaS credentials (Microsoft 365, Salesforce, Slack, AWS), personal accounts (Gmail, socail media used for business), and cryptocurrency/payment credentials (AWS keys, API tokens)
When a customer's credentials surface, Sophos ITDR provides
- Real-time alert (detection within hours of posting, not days)
- Credential exposure details (which account, which service, hash type if encrypted)
- Threat actor context (who is selling, what marketplace, estimated buyer profile)
- Historical check (has this credential been seen before? Has other customer activity been detected?)
- Automated remediation link (one-click password reset or session revocation if MDR/XDR is integrated)
The speed advantage is significant: competitors with batch-mode dark web scanning (daily, weekly) detect credentials after attackers have already exploited them. Secureworks' continuous monitoring detects credentials within hours, enabling prevention
Risk-Based Posture Scoring
Sophos ITDR's Identity Risk Posture score is a benchmark metric enabling organizations to measure identity security improvement over time. The score aggregates:
- High-risk finding: Active threats, configuration risks immediately exploitable, dormant privileged accounts
- Medium-risk findings: Security gaps requiring remediation, compliance violations, non-critical misconfigurations
- Resolved-findings: Issues previously identified and remediated (improving the score)
The score updates daily, enabling organizations to visualize the impact of remediation efforts. This is critical for compliance documentation: auditors can see the organization is continuously improving its identity posture, and CISOs can quantify identity security ROI to executives
Support for Microsoft Entra ID
Sophos ITDR is currently engineered primarily for Microsoft Entra ID environments. Documentation and product marketing emphasize Entra ID integration (Entra ID logs via Event Hub, Entra ID native connectors, Entra ID risk signals integration)
Entra ID is the focus because
- Market Reality: 95% of cloud-deploye organizations use Entra ID; it's the dominant cloud identity platform
- Technical integration: Event Hub integration with Microsoft enables efficient, secure log streaming without agents or complex fiewall rules
- Competitive positioning: Microsoft's ITDR has documented gaps (false positives, incomplete dark web intelligence, incomplete sensor coverage); Sophos ITDR fills these gaps for Entra ID-centric organizations
Future roadmap likely includes extended support for other identity platforms (Okta, Ping, Google Workspace), but current GA focuses on Entra ID
Conclusion
Sophos ITDR represents a fundamental shift in how organizations can approach identity threat detection: moving from fragmented, siloed tools (IAM for governance, SIEM for detection, manual dark web monitoring) to an integrated platform where identity threat detection, behavioral analytics, dark web intelligence, and response automation operate as a unified system.
-
It fills a known market gap Microsoft's ITDR has documented failures (false positives, dark web intelligence in development, heterogeneous environment blindspots). Organizations using Entra ID are actively seeking supplementary ITDR solutions. Sophos ITDR is positioned as the specialist that "fixes what Microsoft missed", not as replacement or threat to existing Entra ID investments
-
Natural Extension of Existing Relationships If you have Sophos MDR or XDR customers, ITDR is a add-on requiring minimal additional infrastructure. If you have Sophos endpoint customers without MDR/XDR, ITDR + XDR creates an upgrade path. If you have no Sophos relationship, ITDR + MDR is a compelling competitive entry point for midmarket customers frustrated with their current identity security.
-
Regulatory Tailwinds NIS2 enforcement is live; DORA applies to financial services. All these regulations mandate "continuous identity monitoring" and "incident response capability" with specific timeframes. Sophos ITDR + MDR directly satisfy these technical requirements and generate the audit evidence organizations need for compliance verification
-
Compelling ROI Sophos ITDR delivers measureable security outcomes
- Mean Time To Detect identity threats: from 292 days to hours or minutes
- False positive reduction: From 95%+ dismissal rate (Entra ID Protection) to behavioral analytics designed for precision
- Labor efficiency: MDR integration eliminates the need to hire dedicated identity analysts; small security teams handle larger environments