OneIdentity PAM
IdentityPAM

Overview
SafeGuard PAM
One Identity Safeguard represents a full-strength, enterprise-grade Privileged Access Management platform delivered as a hardened, secured appliance deployed within your infrastructure. Think of it as a fortress that sits at the center of your privileged access ecosystem, securing and monitoring every high-risk user action before it happens.
This solution integrates three core capabilities into a single architecture:
- Secure Credential Storage and Management (Privileged Passwords)
- Real-time Session Monitoring and Recording (Privileged Sessions)
- Intelligent Threat Detection powered by Machine Learning and Analytics (Privileged Analytics)
Rather than juggling separate point solutions, organizations get a unified system where each component feeds data to the others, creating comprehensive visibility into who is accessing what, when and how.
Safeguard operates as a hardened appliance with full-disk encryption and a stripped-down operating system that removes unnecessary components and disables physical console access. This appliance-based approach means the security infrastructure is locked down from day one, simplifying both deployment and ongoing management. The system can be deployed on-premises within your data center, on you own infrastructure in the cloud, or as a hybrid model with "Approval Anywhere" (a cloud-based workflow that lets security teams approve access requests from any device while the core system remains on-premises)
For organizations managing Unix, Linux and Mac systems alongside Windows environments, Safeguard offers Active Directory integration through an "AD Bridge" that consolidates authentication, eliminating the need for separate identity systems across your organizations
PAM Essentials
One Identity Cloud PAM Essentials represents a radically simplified approach to privileged access management, designed specifically for organizations seeking enterprise-grade security without the infrastructure burden. Rather than deploying and maintaining a hardened appliance, PAM Essentials is a fully managed cloud service where One Identity handles all infrastructure, updates, scaling, and operational complexity while your organization focuses exclusively on access policies and user management.
PAM Essentials delivers core privileged access management functionality through a cloud-native architecture. The solution emphasizes "streamlined PAM", meaning it provides the essential capabilities that protect against the highest-risk scenarios without unnecessary complexity. There is no proxy gateway requirement for session recording, no infrastructure management responsibility, and no capital investment in hardware or data center footprint.
- PAM Essentials natively integrates with OneLogin. Companies already using OneLogin or searching for a mature IAM solution can upgrade to PAM in an easy way
- Every admin account in PAM Essentials also gets access to the Onelogin system, so SSO can also be leveraged for these admin users
The platform implements a Zero Trust architecture where trust is never assumed. Rather than traditional VPN-based remote-access, PAM essentials uses VPN-less secure tunnel technology that creates encrypted connections directly to cloud resources without routing through centralized gateways. This architecture is inherently more secure and significantly simpler to deploy than traditional network access solutions.
Native integration with OneLogin (One Identity's cloud identity platform) provides seamless identity and access management, though the solution also works with other identity providers through standard protocols (SAML, OAuth). For organizations already using OneLogin as their primary identity platform, PAM Essentials becomes a natural extensions requiring minimal configuration.
How to position
Safeguard PAM
Safeguard PAM is purpose-built for larger enterprises and regulated organizations where infrastructure control, data sovereignty, and advanced threat detection are non-negotiable. The primary customer profiles include:
- Financial Services and Healthcare Institutions: These sectors operate under strict regulatory frameworks and often have data residency requirements mandating that sensitive access logs and credentials remain within their own infrastructure. Safeguard's on-premises appliance directly addresses this requirement, allowing organizations to maintain complete control over where privileged access data is stored and processed
- Government and Defense Contractors: Organizations handling classified information or operating in high-security environments require teh transparency, auditability, and control that comes with an on-premises solution. The comprehensive session recording with keystroke capture and OCR-enabled search creates forensic evidence suitable for security clearance processes and government audits
- Large Enterprises with Segmented Networks: Organizations with air-gapped networks, disconnected data centers, or complex network segmentation find that Safeguard deploys more easily than solutions requiring centralized cloud infrastructure. Each appliance operates independently while clustering for redundancy, making it ideal for organizations where network boundaries are security features, not obstacles
- Existing One Identity Customers: The seamless integration with One Identity's Identity Manager and Identity Governance Administration (IGA) platform creates a natural expansion path. Organizations already managing identity lifecycle through One Identity's broader platform see significant efficiency gains from deeply integrated PAM controls
- Organizations Requiring Advanced Threat Detection: Companies concerned about insider threats, advanced persistent threats, or needing to demonstrate sophisticated threat monitoring for cyber insurance purposes require Safeguard's machine learning analytics. The pattern-free analysis and behavioral biometrics are distinct differentiators
PAM Essentials
PAM Essentials is optimized for organizations where simplicity, rapid deployment, and cost-effectiveness matter more than granular customization. The primary customer profiles include:
- Small to Medium-Sized Businesses (SMBs): SMBs typically lack dedicated security operations teams and cannot afford the infrastructure management overhad of on-premises PAM solutions. PAM Essentials elmiminates infrastructure complexity entirely - there is no appliance to deploy, patch or monitor. Security teams focus on defining access policies while the cloud service handles everything else
- Cloud-First and Hybrid Organizations: Companies built on AWS, Azure or Google Cloud find that PAM Essentials' cloud-native architecture integrates naturally with their infrastructure. The VPN-less secure tunnel technology means remote workers and hybrid teams can access privileged resources without complex network engineering
- Distributed and Remote-First Workforces: Organizations with teams spread across multiple locations, significant contractor/vendor populations, or hybrid work models require solutions that work seamlessly from anywhere. PAM Essentials' cloud delivery and VPN-less secure access are purpose-built for these scenario's.
- Budget-Constrained Organizations: Companies preferring predictable operational expenditures (OpEx) over capital expenditures (CapEx) find the SaaS subscription model more attractive than hardware investments. There is no appliance purchase, no infrastructure buildout, no staff time for maintenance - just a annual subscription
- Organizations with limited IT/Security Staff: Understaffed security teams cannot afford to hire specialists to manage infrastructure. PAM Essentials' fully managed model allows a security team of any size to enforce sophisticated privileged access controls without operational burden
- Organizations Using OneLogin: If your organization has already standardized on OneLogin for identity and access management, PAM Essentials becomes the natural choice, the integration is built-in, reducing configuration effort and improving the user experience.
Core Features
One Identity Safeguard PAM
Safeguard for Privileged Passwords
This component functions as a sophisticated, role-based credential vault that automates the process of securely storing, requesting and rotating privileged account passwords. Rather than admin passwords being scattered across spreadsheets, email or personal notes, all credentials flow through a controlled, auditable process
The module discovers privileged accounts across your network using three methods:
- Host-based discovery (scanning individual systems)
- Directory-based discovery (querying Active Directory and LDAP)
- Network-based discovery (scanning for systems with administrative protocols) Once discovered, these accounts are securely stored in an encrypted vault on the hardened appliance
A standout feature is the "personal password vault" available to business users at no additional cost. This allows employees to store non-critical passwords (like personal cloud services used for work) securely, reducing the temptation to reuse credentials across systems
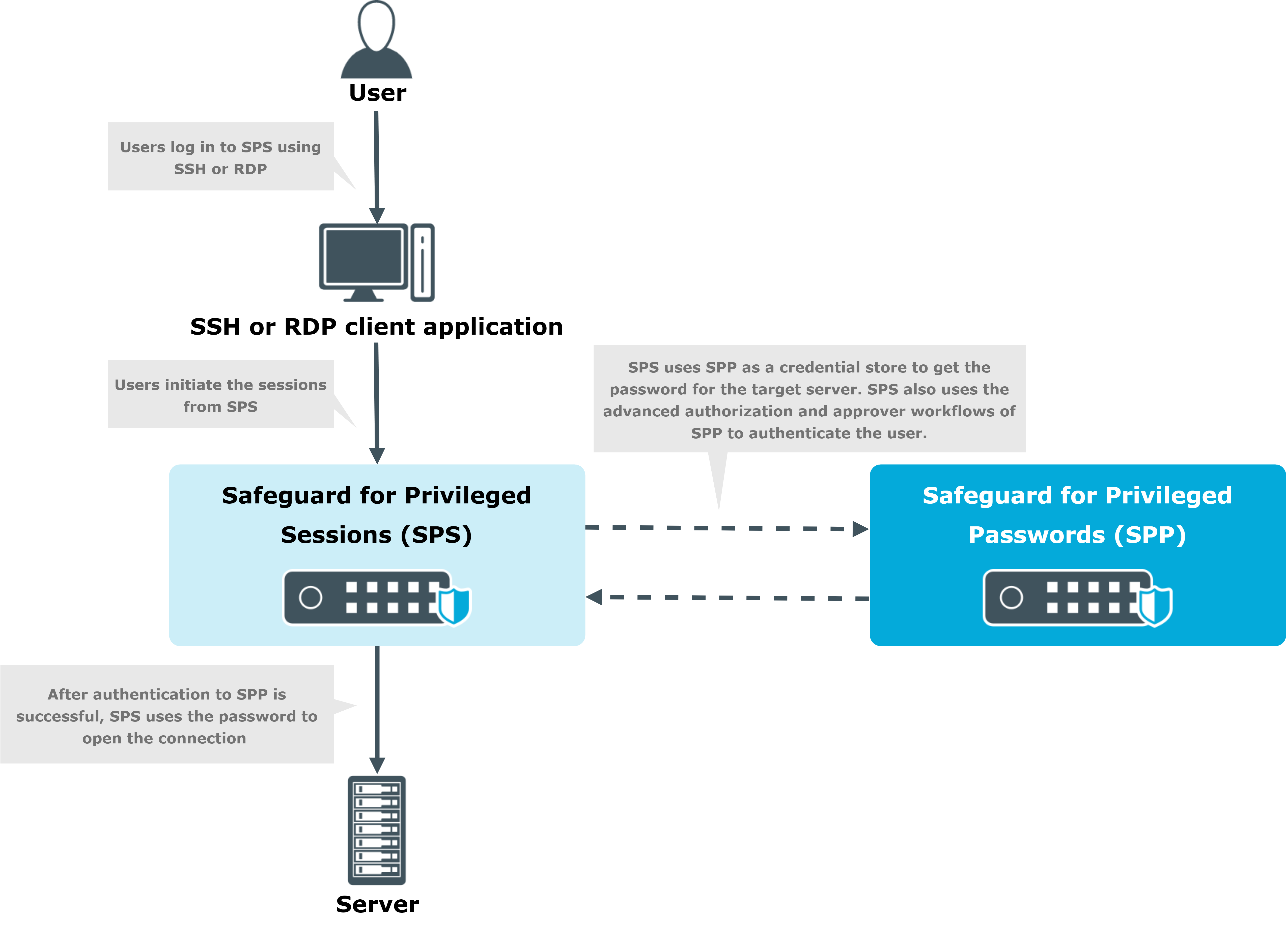
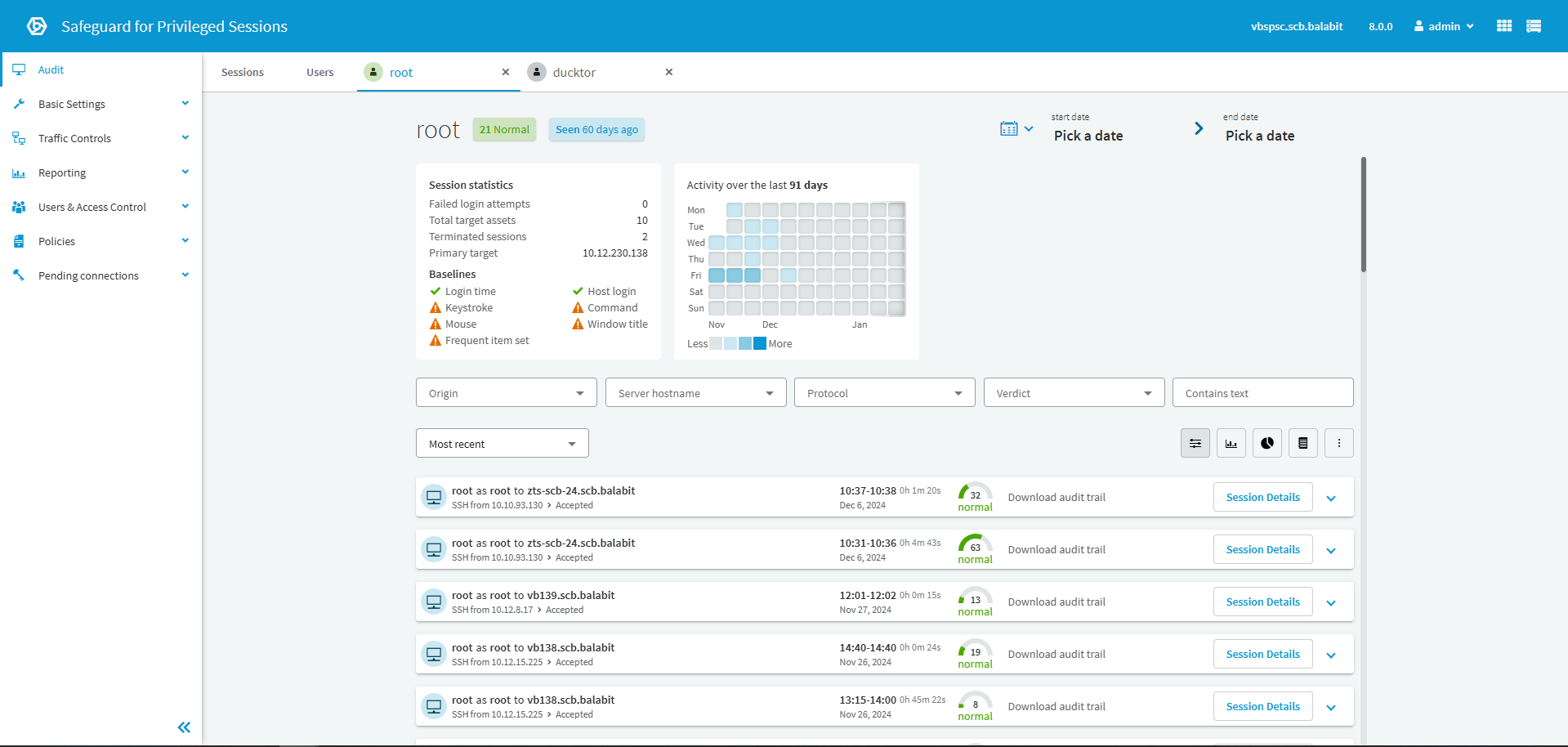
Safeguard for Privileged Sessions
This component records and monitors every action of privileged users in real time, acting as an application-level proxy that sits between the user and the system they're accessing. The system captures keystroke-level activity, mouse movements, windows viewed, and file operations. Critically, all this data is indexed and searchable, you can query sessions like a database while also reviewing them like a video recording.
The proxy functionality is sophisticated: it inspects protocol traffic at the application layer, allowing security teams to write rules that block specific commands or window tiles based on predefined policies or detected risk. For example, rules can automatically block attempts to dump the Active Directory database or access sensitive files outside normal business hours. When violations occur, the system can alert security teams or automatically terminate the session.
Session recording supports multiple protocols: SSH (for Unix/Linus), Telnet, RDP (for Windows), HTTP/HTTPS, ICA (Citrix) and VNC. The recorded content is indexed to enable powerful searches. You can search for specific SQL commands across all sessions, or locate all instances where a particular file was accessed.
The OCR (Optical Character Recognition) engine enables full-text search of screen content, making it possible to find sessions based on what users saw or typed, not just metadata. This transforms post-incident forensics from "find the session where this happened" into "find all sessions containing this text."
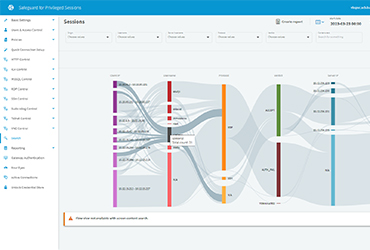
Safeguard for Privileged Analytics
This machine learning-powered component analyzes the behavioral patterns of privileged users to detect anomalies that suggest compromise, insider threats, or unusual activities. Unlike traditional rule-based systems that look for specific attack signatures, Safeguard's analytics operate "pattern-free": they learn what normal looks like for each user and flag deviations as potential threats.
The system employs multiple algorithms, working in parallel:
- Keystroke Dynamics Algorithm: Every person has a unique typing pattern, the rhythm of key presses, release timing, and finger movement. The system learns an individual's baseline typing pattern and can detect when someone else is using that account by comparing keystroke timing against the learned profile. This provides continuous, biometric-level authentication even during active sessions
- Mouse Movement Algorithm: Similar to keystroke dynamics, user behavior analytics track distinctive patterns in mouse movement, acceleration, and cursor patterns to identify when sessions deviate from normal behavior.
- Scripted Session Detection: Attackers often automate attacks using scripts that execute actions with inhuman precision and timing. The "clockmaster" algorithm detects unnaturally precise timing, for example, a script that initiates database queries every 8 minutes exactly. The "gapminder" algorithm identifies unexpected gaps in user activity that suggest automated processes.
Each algorithm scores sessions independently, and the scores are aggregated (with highest and lowest scores removed to prevent outliers) to create a final risk score. Sessions scoring 80-100 indicate highly anomalous behavior requiring immediate investigation. The system ranks alerts by risk level, reducing false positives and allowing security teams to focus on the most critical threats.
PAM Essentials
Sessions-Based Privileged Access
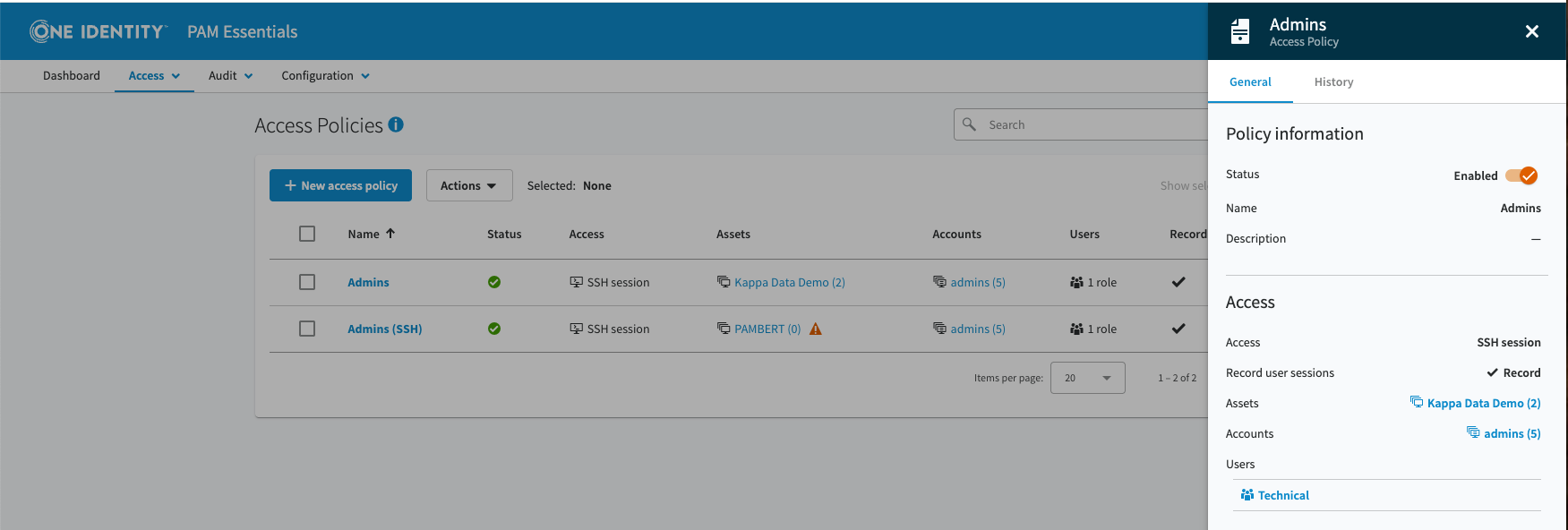 This component provides granular control over who can access which privileged resources and how those session are managed. Rather than giving users standing access to systems (the old "shared admin account" model), PAM Essentials creates discrete, auditable sessions where access is granted on-demand and recorded continuously.
This component provides granular control over who can access which privileged resources and how those session are managed. Rather than giving users standing access to systems (the old "shared admin account" model), PAM Essentials creates discrete, auditable sessions where access is granted on-demand and recorded continuously.
Sessions are controlled through role-based access control (RBAC) that integrates with your existing Active Directory or identity provider. Users are assigned roles that determine which resources they can access, and access requests flow through defined workflows. A junior administrator might have standing approval for non-production database access, while production database access requires a manager's approval.
The module supports SSH and RDP protocols for traditional system access, and extends control to SaaS applications, meaning organizations can record and control access to cloud services, not just on-premises systems. This is particularly valuable as organizations shift towards SaaS-first tooling.
Centralized session monitoring provides real-time visibility into active privileged sessions. Security teams can see who is connected to which systems, for how long, and from where. This visibility enables quick response if suspicious activity is detected.
Privileged Session Recording
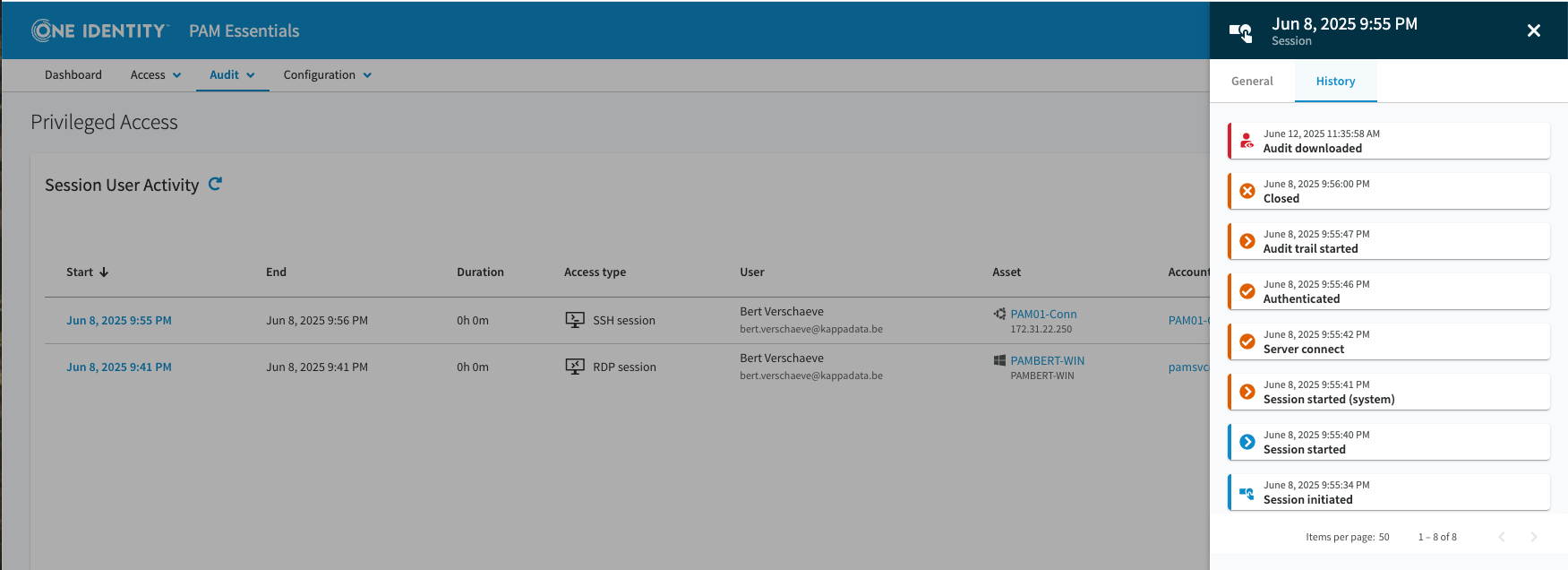
PAM Essentials records all privileged sessions using protocol proxy recording, capturing everything that happens during access. This provides a complete audit trail suitable for compliance investigations, security incident response, and user behavior analysis.
Session isolation prevents lateral movement. If a user's credentials are compromised during a recorded session, the isolation ensures the attacker cannot jump to other systems. All session activity remains contained and recorded.
The system creates structured audit logs that capture systematic records of all activities, events, and changes. Unlike raw log files that require technical expertise to parse, structured logs are immediately useful for compliance reporting and forensic investigation. Integration with access management ensures that when users are provisioned and deprovisioned in your identity system, those changes automatically flow through to access termination in PAM Essentials.
Secure Credentials Management
Rather than users manually entering credentials (or storing the minsecurely), PAM Essentials automates credential management through several mechanisms.
Auto-login (credential injection) automatically supplies credentials during session initiation. Users request access through the portal, and when the session opens, credentials are automatically supplied. Users never see the actual password, reducing the risk of credential compromise.
Local server account passwords are secured through vaulting. Instead of admins managing server root/local administrator passwords manually, the system centrally stores these credentials and provides access on-)demand. This eliminates the dangerous practice of shared passwords or passwords written on whiteboards.
Automated password rotation on defined schedules ensures credentials are regularly changed without manual administrator effort. The system can rotate the passwords hourly, daily or on custom schedules. This dramatically reduces the window of opportunity if a credential is compromised.
Surveillance of out-of-band password changes detects when credentials are changed outside the normal PAM Essentials process. If an administrator manually changes a password using the system directly (rather than through PAM Essentials), the system detects this and generates an alert. This prevents shadow password management and maintains a single source of truth for credentials.
VPN-Less Secure Tunnel Technology
This is perhaps PAM Essentials' most distinctive feature and directly addresses a major pain point in traditional PAM deployments. Rather than requiring users to connect to a corporate VPN before accessing privileged resources, PAM Essentials enables direct, encrypted connections from user devices to cloud resources through secure tunneling.
The secure tunnel operates at the application layer rather than the network layer, providing more granular security controls. Authentication and authorization occur before any connection is established, enforcing Zero Trust principles (trust is never assumed; all access requests must be verified)
The architecture directly connects to cloud-based resources without routing through centralized gateway infrastructure. This simplification provides multiple benefits: faster performance (no gateway latency), easier scaling (no gateway capacity planning), and reduced operational complexity (no gateway to patch or monitor).
Users accessing privileged resources experience a frictionless workflow: they authenticate to OneLogin, request the resource they need through the PAM Essentials portal, and are immediately connected to the target system. No VPN client installation, no complex network configuration, no session timeouts due to network connectivity issues.
Feature Overview
Safeguard PAM
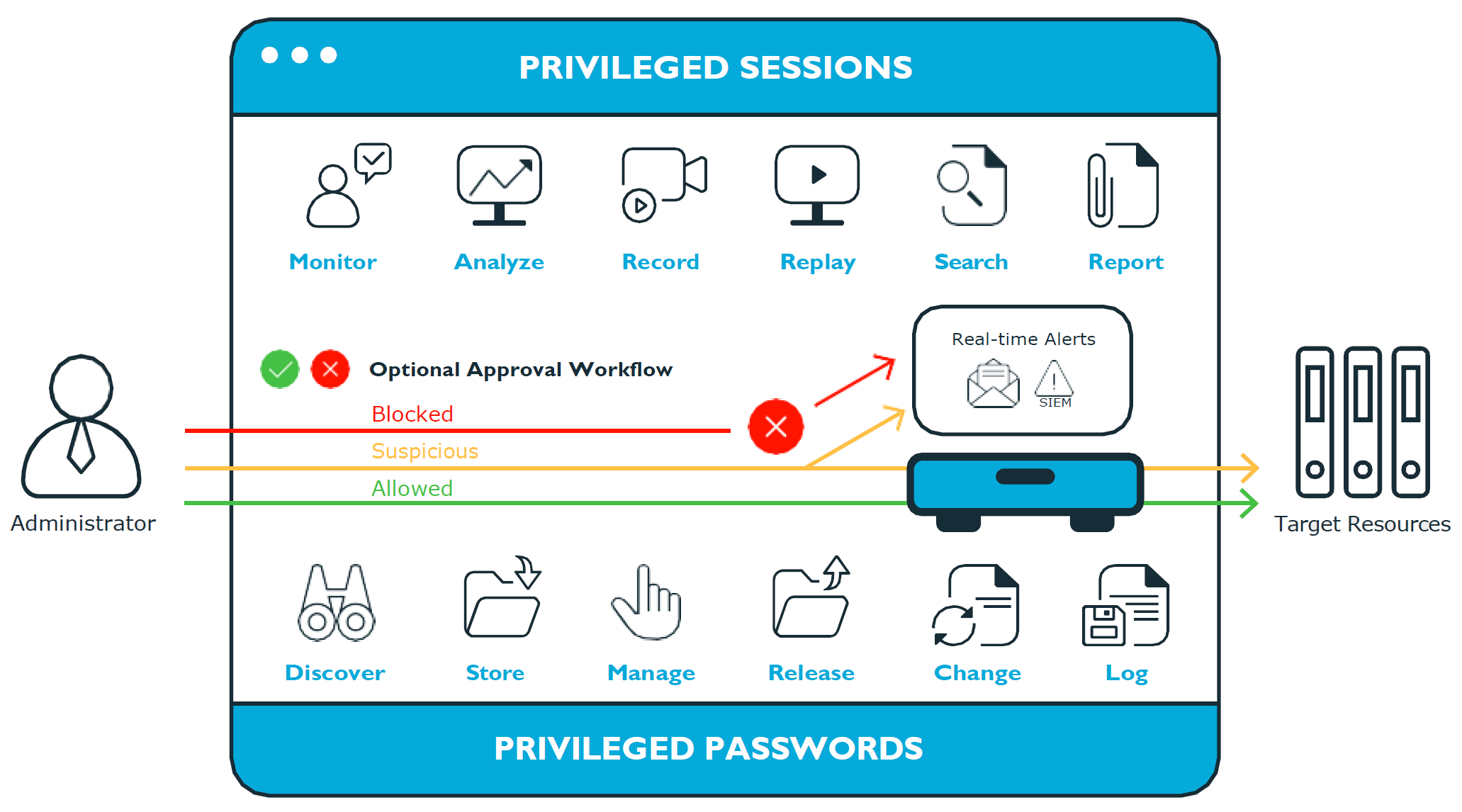
Deployment and Architecture
- Available as physical hardened appliance or virtual machine
- Hardened, stripped-down operating system with full-disk encryption
- Can operate standalone or in clusters for high availability
- "Approval Anywhere" cloud component for workflow approval from remote locations
- Support for hybrid deployments with cloud-based components
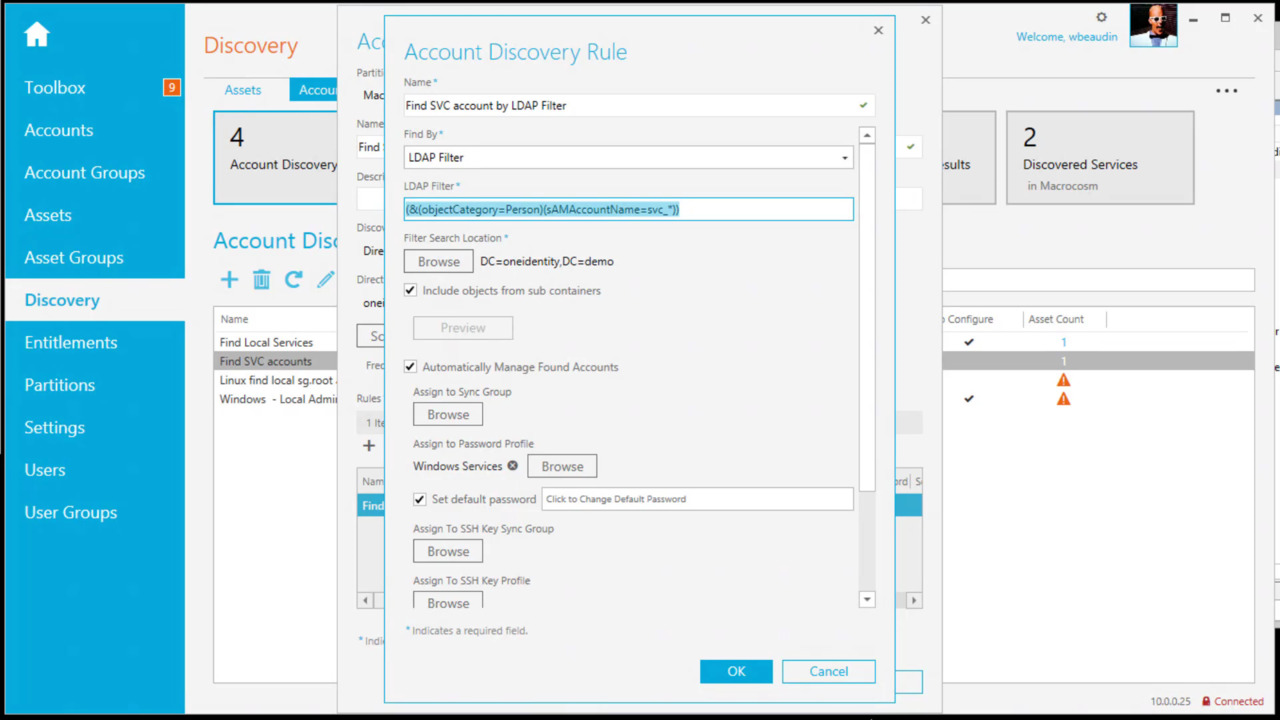
Credential Management Capabilities
- Automatic account discovery across network (host, directory, network-based)
- Role-based access control with approval workflows
- Automated password rotation on schedules (time-based, last-use based, manual, forced)
- REST API for integration with third-party systems
- Multi-factor authentication for vault access
- Personal password vault for business users
- Mobile approval interface for authorized users
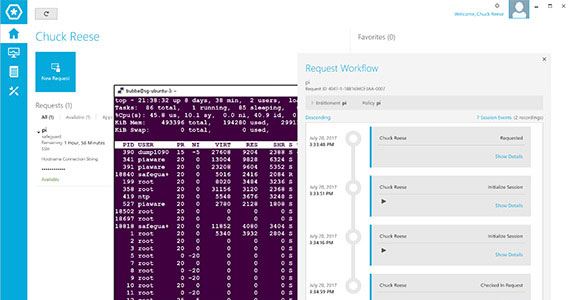
Session Recording and Monitoring
- Full keystroke, mouse and screen capture
- Protocol support: SSH, Telnet, RDP, HTTP(S), ICA, VNC
- Application-level protocol inspection
- Real-time alerting and automatic session termination
- Black-list and white-list command/window title policies
- Transparent deployment (no changes to user systems) or workflow-based
- Indexed, searchable session database with OCR
- Video-like playback with granular search
- File operation tracking and transfer extraction
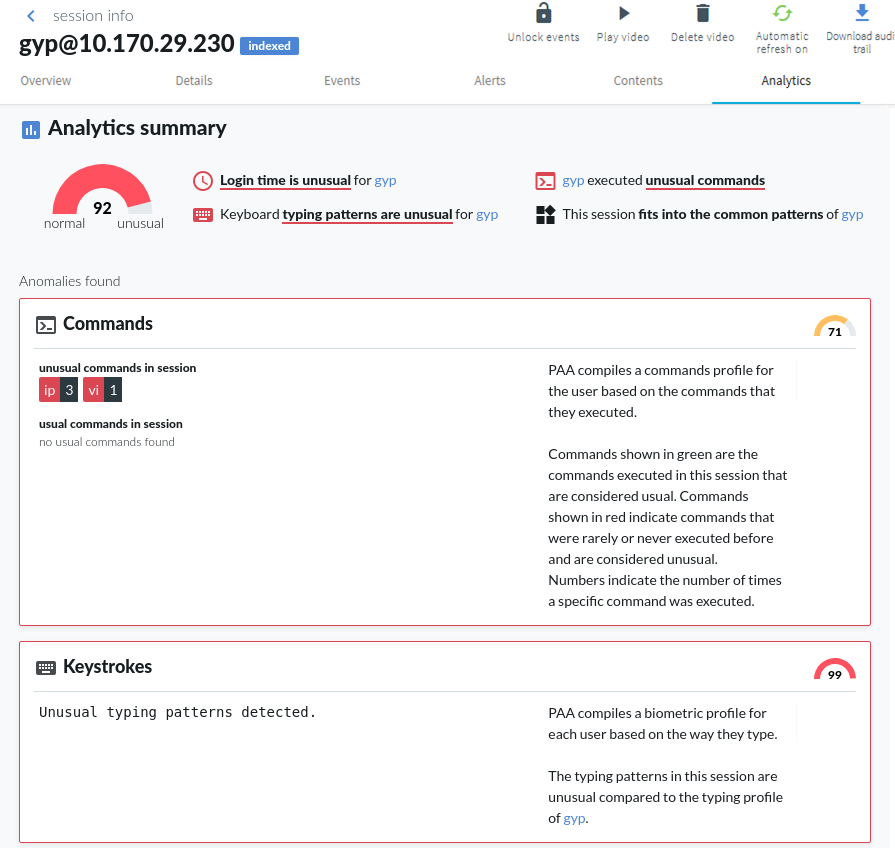
Analytics and Threat Detection
- Machine learning anomaly detection (pattern-free)
- Multiple concurrent algorithms (keystroke dynamics, mouse movement, scripted session detection)
- Risk-ranked alerts with severity classification
- User behavior profile generation
- Continuous biometric authentication capability
- Integration with SIEM platforms
- Full-content analysis (commands, screen content, window titles)
Compliance and Audit
- Encrypted, time-stamped, cryptorgraphically signed audit trails
- Forensic-level investigation support
- Comprehensive compliance reporting
- Session replay capability with full-text search
- OCR-enabled audit log searching
- Evidence preservation for regulatory investigations
PAM Essentials
Deployment and Architecture
- Fully managed SaaS cloud deployment with no infrastructure installation required
- Cloud-native archiecture enabling automatic scaling
- VPN-less secure tunnel technology for direct resource access
- Zero Trust architecture with continuous authentication
- Native OneLogin integration
- Rapid deployment
Session and Access Control
- Full SSH and RDP integration for traditional systems
- SaaS application control and recording
- Centralized session monitoring and management
- Role-Based Access Control (RBAC)
- Active Directory integration for user/group management
- Transparent user experience with minimal friction
- Application-level security controls
- Session isolation to prevent lateral movement
Session Recording and Compliance
- Protocol proxy session recording for SSH and RDP
- SaaS application session recording
- Structured audit logs with systematic activity records
- Integration with access management for provisioning/deprovisioning workflows
- Forensic-level visibility into user activities
- Compliance-ready audit trails
- Session data suitable for regulatory investigations
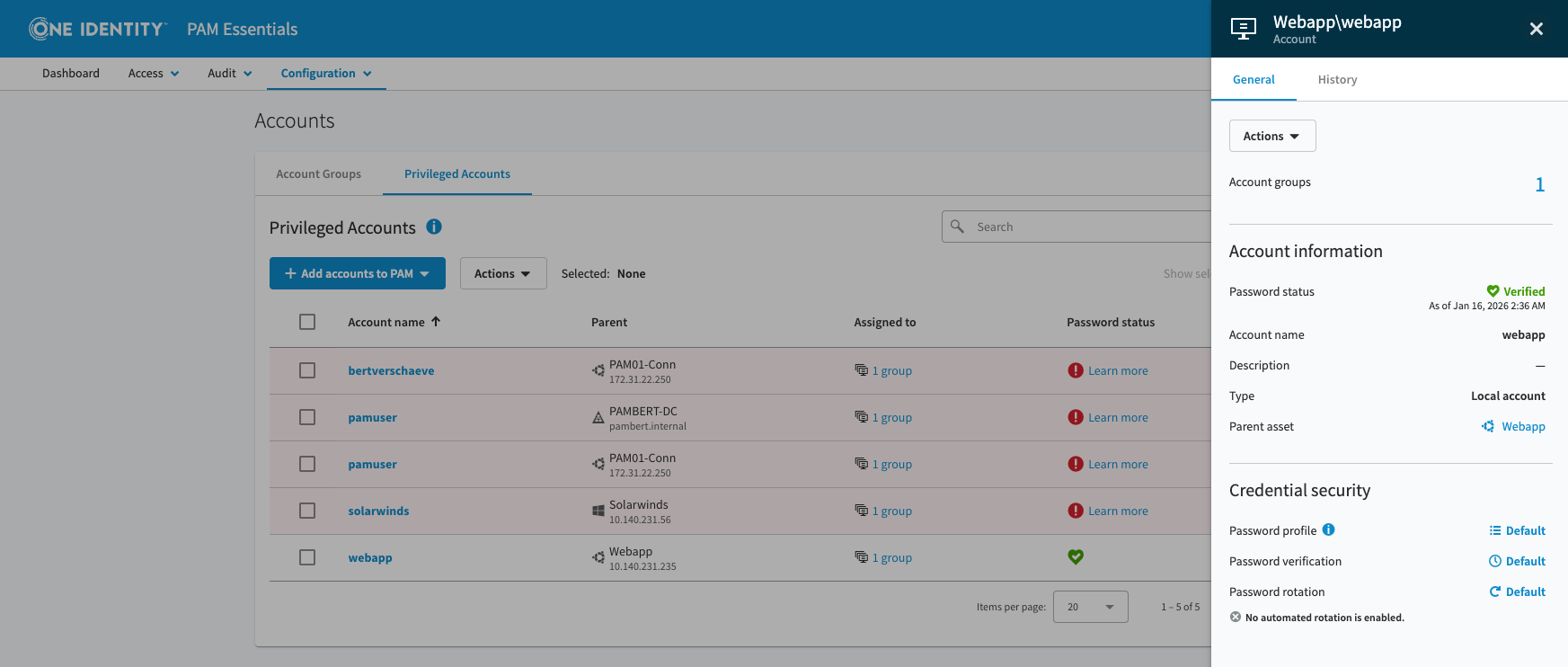
Credentials Management
- Auto-login (credential injection) eliminating user password visibility
- Secure vaulting of local server account credentials
- Automated password rotation on defined schedules
- Surveillance of out-of-band password changes
- Centralized credential lifecycle management
- Integration with ITSM systems for change management
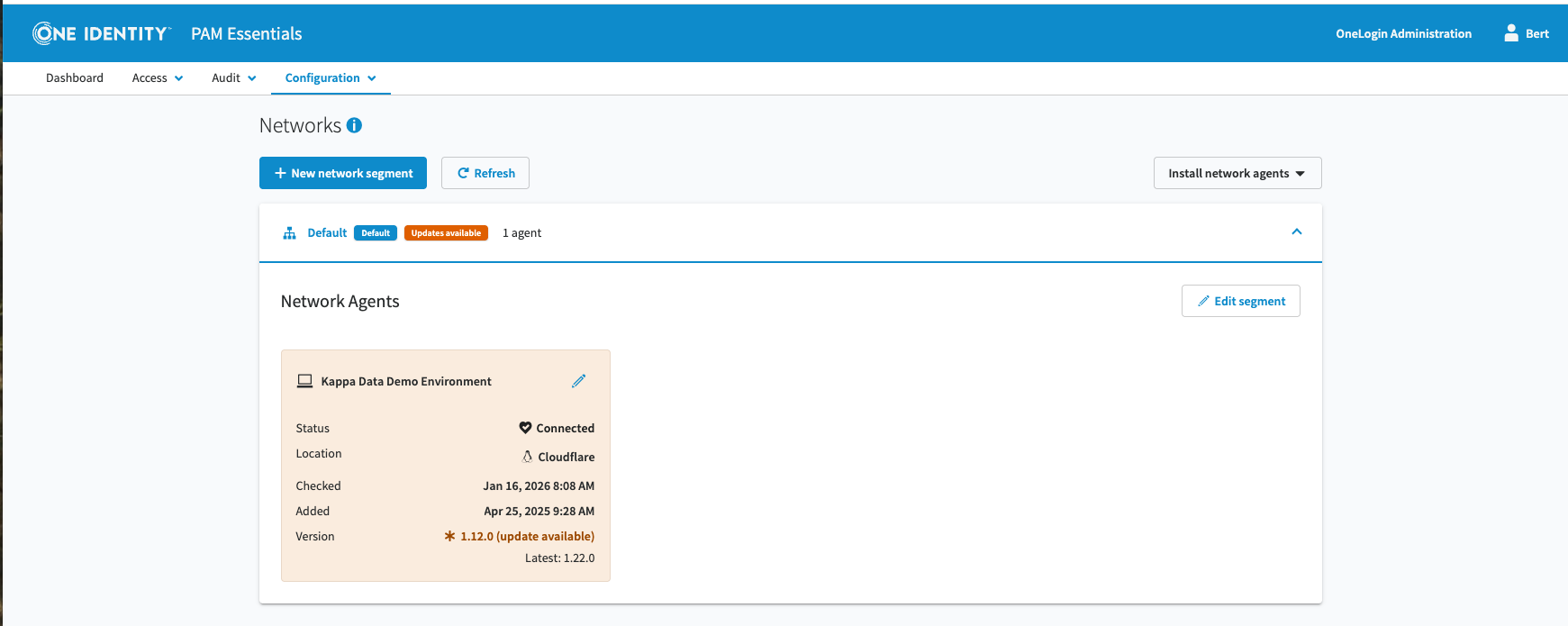
Network and Access
- VPN-less secure remote access
- Zero Trust architecture with verification of every request
- Direct cloud resource connections with gateway routing
- Application-level security controls
- Seamless experience for remote and hybrid workers
- Enhanced privacy and data protection
- Support for contractors, vendors and extended teams
Integration and Operations
- Native OneLogin integration
- ServiceNow, Slack, Teams integration for approvals
- REST APIs for custom integrations
- Minimal operational overhad (fully vendor-managed)
- Automatic security updates and patches
- Built-in high availability and disaster recovery
When Choose what?
The choise between Safeguard PAM and PAM Essentials reflects different organizational priorities.
- Safeguard PAM is the correct choice when infrastructure control, advanced threat detection, and maximum customization are paramount. These are organizations willing to accept operational complexity in exchange for complete visibility and control.
- PAM Essentials is the correct choice when rapid deployment, operational simplicity and cost-effectiveness matter more than granular customization. These are organizations willing to accept some feature limitations in exchange for eliminating infrastructure burden