OneIdentity IGA
Identity IGA
Overview
One Identity's Identity Governance and Administration (IGA) portfolio represents a comprehensive approach to managing digital identities, access permissions, and security policies across enterprise environments. The platform enables organizations to enforce the principle of least privilege (granting users access only to resources necessary for their roles), while maintaining visibility, control and compliance across on-premises, hybrid and cloud infrastructures.
The One Identity IGA suite consists of five core products:
- Identity Manager (the foundational on-premises platform)
- Identity Manager On Demand (+ starling edition) (Cloud-native SaaS offering)
- Identity Manager Data Governance Edition (specialized module for unstructured data access)
- Starling Connect (cloud provisioning connector)
Each product addresses distinct deployment and governance scenarios, allowing organizations to select solutions aligned with their infrastructure maturity and compliance requirements
How to position
One Identity IGA solutions specifically target enterprise organizations with three key characteristics: complexity, compliance burden, and distributed infrastructure
Primary Target Segments
- Large Enterprises represent the core market. These organizations typically operate complex identity ecosystems with multiple legacy systems, enterprise applications, and cloud platforms that require unified governance. The investment in IGA infrastructure becomes economically justified when managing thousands of identities across hundreds of systems.
- Highly Regulated Industries including financial services, healthcare, insurance, and pharmaceuticals form a second critical segment. These industries operate under strict regulatory frameworks where compliance violations carry material business risk. One Identity Manager directly addresses these requirements through automated attestation/recertification, segregation of duties enforcement, and comprehensive audit trails that accelerate compliance cycles
- Hybrid and Multi-Cloud Organizations represent growing demand drivers. Companies transitioning from on-premises infrastructure to hybrid models require an IGA platform capable of governing access across environments simultaneously. Traditional on-permises IGA tools struggle with cloud governance, and pur cloud-first solutions often lack the depth needed for complex on-premises systems. One Identity's deployment flexibility addresses this directly
- Technology and Services Companies with complex SAP environments present a specialized but substantial opportunity. One Identity Manager includes SAP-certified integration with deep capabilities to import and govern SAP transaction usage data, enabling organizations to enhance existing SPA security models while connecting accounts under unified governance
The following opportunities could also be interesting to look into:
- Consolidation Play: Organizations currently operating 3+ IGA tools or managing IGA through fragmented point solutions represent immediate early-win targets. These customers understand IGA value but suffer from integration debt, redundant work, and inconsistent policies. Consolidating onto One Identity Manager immediately delivers ROI through operational efficiency
- Compliance Crisis Response: Companies facing failed audits, regulatory findings, or significant access review backlogs experience acute pain around current solutions' inability to automate compliance workflows. These organizations demonstrate urgent budget availability and compressed decision timelines. Demonstrating how One Identity Manager's automated attestation, recertification scheduling, and SoD detection resolve these pain points - often within initial pilot phases - creates rapid traction
- Legacy Active Directory Management: Many enterprises use basic AD management tools lacking sophisticated governance. These organizations recognize AD security risks but haven't invested in comprehensive IGA. Positioning Identity Manager as an evolution of existing AD infrastructure (rather than a replacement) lowers perceived complexity and eases internal advocacy
- Think of One Identity as a comprehensive governance platform for complex enterprises, while JumpCloud is a simplified directory/device management platform optimized for speed and cost efficiency at the SMB and mid-market level
- One Identity operates on a governance-first model. The platform assumes organizations need to defend complex access patterns against regulatory scrutiny
- JumpCloud operates on a simplicity-first model: cloud-native directory replacing Active Directory, unified device management across operating systems, straightforward SSO/MFA and rapid deployment. The platform assumes organizations value speed and cost over governance complexity
Core Features
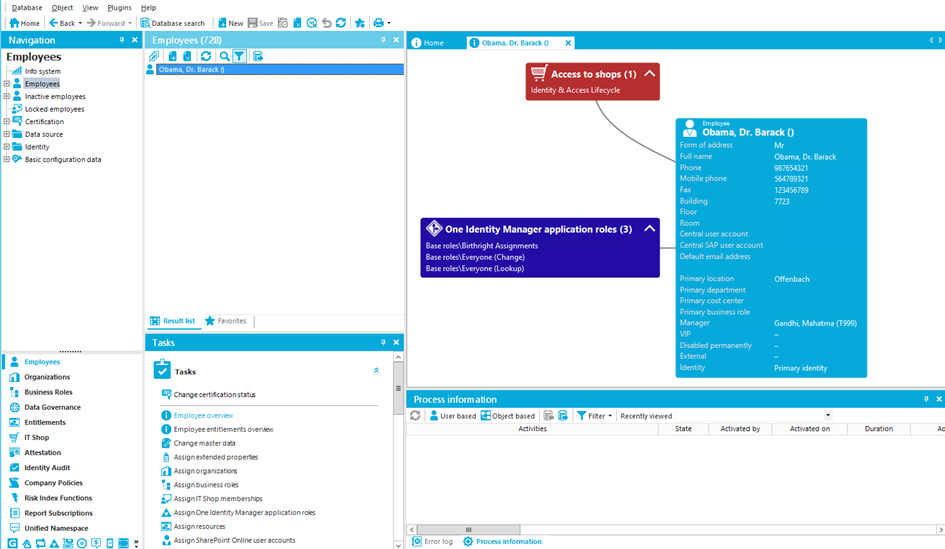
Identity Manager (On-Premises Platform)
Identity Manager serves as the foundational IGA platform designed to simplify identity management processes while reducing IT administrative burden. The product operates on an automation-optimized architecture that addresses core Identity Governance and Administration challenges at substantially lower complexity compared to traditional solutions.
The platform functions through a centralized database that represents the core of the system, fulfilling primary tasks of managing identity data and calculating inheritance relationships across roles and permissions. From this database, Identity Manager provides unified control over the complete identity lifecycle, from user onboarding through role changes to offboarding, regardless of whether resources exist on-premises, int he cloud, or in hybrid environments.
Key architectural components include:
- Manager: The primary administration tool for configuring all identity data, managing user accounts, permissions, and company-specific roles across the network
- Web Portal: A modern, user-facing interface enabling self-service access requests, password resets, and attestation participation
- Job Server: Performs background data synchronization between connected systems and executes policies at the database level
- Connector Framework: Enables connectivity to target systems ranging from Active Directory to enterprise applications via 100+ pre-built connectors and PowerShell-based custom connectors
The platform supports role hierarchies and inheritacne, allowing organizations to model complex organizational structures where roles can inherit permissions from parent roles. This capability proves particularly valuable in large enterprises where permissions must cascade naturally across management tiers.
Identity Manager On Demand & Starling Edition
- Identity Manager On Demand is a fully-managed SaaS version of Identity Manager, deployed through One Identity's cloud infrastructure. This model eliminates infrastructure management burden. One Identity's operations team handles hosting, maintenance and security
- Identity Manager On Demand Starling Edition: represents the modern evolution of the cloud offering, delivered as a Starling service integrated into the unified One Identity Starling platform. Starling Edition provides identical IGA functionality to on-premises versions without compromising features or scope, yet eliminates the operational complexity of managing infrastructure.
Both cloud variants deliver the same core capabilities as on-premises Identity Manager but offer advantages in deployment speed, scalability and operational management. Organizations can establish a functioning IGA environment in weeks rather than months, as cloud instances are pre-configured and immediately accessible. The SaaS model also provides automatic updates, eliminating the need to manage upgrae cycles manually.
Identity Manager Data Governance Edition
This specialized module extends Identity Manager's governance capabilities speifically to unstructured data - files, folders, shares and repositories that exist outside traditional application-based access control systems. Many organizations recognize that 80% of enterprise data exists as unstructured files, yet governance tools rarely address this category adequately
Data Governance Edition enables:
- Access analysis of unstructured data across NTFS, NAS devices and SharePoint environments
- Owner identification through usage pattern analysis to assign appropriate business owners for future governance
- Classification of sensitive data with risk levels to prioritize protection efforts
- Self-service request workflows allowing employees to request access to specific files/folders with automated routing to appropriate data owners for approval
- Attestation and recertification where business owners periodically verify who should and should not have access to governed data
The module operates within Identity Manager's existing architecture, leveraging the same authentication, workflow and reporting engines. Organizations can deploy it standalone if focused primarily on data governance, or combine it with full Identity Manager for comprehensive identity and data governance
Starling Connect
Starling connect functions as a cloud-based provisioning connector and synchronization bridge that extends existing on-premises identity governance to cloud applications. Rather than requiring custom development for each cloud application. Starling Connect uses standardized SCIM (System for Cross-domain Identity Management) protocols to automate user provisioning and group synchronization across SaaS platforms.
Organizations leverage Starling Connect to:
- Reduce cloud application onboarding time from months to weeks
- Consolidate access control policies for hybrid environments spanning on-premises and cloud resources
- Provision users and groups through standard SCIM interfaces without custom coding
- Generate real-time reports on cloud resource access and user entitlements
- Maintain governance decisions made in Identity Manager across cloud applications
Starling Connect integrates directly with Identity Manager On Demand via Starling Hybrid Subscription, creating a synchronization project that maps identity data between on-premises systems and clodu applications.
- Think of identity security as a two-stage process
- IAM is the bouncer at the nightclub. It verifies you're really John Smith, checks your ID (MFA) and lets you through the door
- IGA is the compliance auditor the next morning: it review whether John Smith should have actually been allowed in, whether he still needs access weeks later, and whether his permissions violate any company rules
- Onelogin and Identity Manager are complementary products operating at different layers.
- Organizations typically implement OneLogin first (fast, handles access granting), then add Identity Manager later when they need governance
- PAM solves a different problem: protecting accounts with elevated permissions. Regular users accessing Salesforce? Onelogin handles that. Admin accounts accessing production databases, That's PAM's job.
Feature Overview
Identity Lifecycle Managmeent
One Identity Manager provides comprehensive automation across the entire identity lifecycle, reducing manual processes that introduce errors and create security gaps
- Provisioning: When new employees onboard, Identity Manager automates account creation across all connected systems. The platform integrates with HR systems to receive employee data, then automatically provisions accounts in Active Directory, cloud applications, email systems, and specialized enterprise systems based on defined business rules. Administrators define provisioning policies mapped to organization roles and shared resource permissions aligned with their job function, without manual ticket processing
- Role-Based Assignment: Rather than assigning access permission-by-permission, Identity Manager uses role hierarchies that reflect organizational structure. Roles inherit permissions from parent roles, reducing configuration complexity. Administrators define roles representing job functions and assign users to these roles, inheriting all associatd permissions. When someone changes roles, their access automatically adjusts to reflect their new function
- Deprovisioning: When employees leave, transfer departments, or complete project assignments, Identity Manager automatically revokes access across all systems. This immediate deprovisioning prevents the common security risk of orphaned accounts retaining permissions long after employees depart. The platform triggers deprovisioning through HR systems integration (detecting termination records) or manual workflow completion, removing access from on-premises systems and cloud applications simultaneously
- Self-Service Capabilities: Employees can request access to resources through a modern web portal without IT involvement for every transaction. Request workflows route access decision to appropriate managers based on business rules. For example, requests for sales tools automatically route to the sales department head for approval. Approved requests automatically fulfill through provisioning workflows
- Attestation and Recertification: Compliance regulations require periodic verification that employees have appropriate access. Traditional recertification processes are manual and tedious - managers receive spreadsheets and approve or deny each access entry individually. One Identity Manager automates this through customizable attestation policies that specify which objects require certification, how frequently and by whom
- Segregation of Duties (SoD) Detection: Financial fraud and security breaches often involve toxic combinations of permissions. One Identity Manager continuously monitors user entitlements against configured SoD policies. When conflicts emerge, administrators either automatically remove conflicting access or document business justifications for the exception
- Risk Scoring: The platform ingests internal ane external risk indicators to prioritize remediation efforts. Security scores from identity analytics tools inform governance decisions. Users displaying risky behavior patterns (impossible travel, unusual login times) might have access restricitons tightened. Organizations using OneLogin access management integrate behavioral insights directly into Identity Manager governance policies, enabling truly risk-driven access desisions
- Workflow Automation & Business-Driven Governance: Identity Manager emphasizes placing governance decisions in the hands of business process owners rather than IT administrators. This shift recognizes that managers best understand who legitimately needs access to resources for their roles
- Customizable Approval Workflows: Organizations define multi-level approval hierarchies. Access requests might require immediate manager approval for standard tools, but escalate to department heads for sensitive systems and CFO sign-off for financial applications. The platform enforces these workflows automatically, routing requests to appropriate approvers and escalating if approvals don't complete within defined timeframes
- Policy-based automation: Rather than routing every request manually, policies automate routine approvals. For example, policies can automatically approve requests for standard role-appropriate access when specific conditions exist. This reduces manual work while maintaining control over high-risk decisions
- Exception Handling: The platform supports documented exceptions where business requirements override default policies. When approvers deny requests that users need for legitimate business purposes, they can document the exception and escalate for executive review. This creates audit-ready documentation of policy exceptions with clear justification
- Comprehensive dashboard: One Identity Manager provides personalized dashboards showing governance status, certification progress, policy violations, and high-risk accounts. Different user roles see different dashboard information.
- Audit-Ready Reporting: The platform generates compliance reports pre-formatted for regulatory reviews. Reports demonstrate adherence to several standards, showing which users accessed which resources when and why. Attestation reports prove that managers certified access appropriately. Certification reports document compliance across all required systems
- Starling Connect SCIM Provisioning: Cloud applications implement SCIM (System for Cross-domain Identity Management) standards for user provisioning. Starling Connect acts as a provisioning bridge, synchronizing identity data from Identity Manager to cloud applications using standard SCIM APIs. Organizations can add new cloud apps to governance without custom development. Just configure the SCIM endpoint and Starling Connect handles ongoing provisioning
- Clou Data Governance: Data Governance Edition extends governance to cloud storage including Microsoft SharePoint Online and OneDrive, addressing cloud-first organizations' needs to govern unstructured data stored in cloud repositories
- Unstructured Data Discovery and Classification: This module analyzes files, folders, and shares across NTFS, NAS and SharePoint environments to discover what data exists and who currently accesses it. Organizations manually classify data by sensitivity levels (public, internal, confidential, restricted) and the platform assigns risk levels accordingly
- Access Request and Approval Workflows: Employees requesting access to governed files submit requests through a self-service portal. Requests automatically route to identified data owners for approval. This shifts data access governance from IT administrators (who lack business context for whether access is appropriate) to business owners who understand whether users legitimately need access
- Owner Identification: The module analyzes historical access patterns to identify appropriate business owners for each governed resrouce. If certain users consistently modify files and others consistently reference their work, the system suggests the modifier as the likely owner, simplifying the owner assignment process.
| Feature | Identity Manager (On-Prem) | Identity Manager On Demand | Starling Edition | Data Governance Edition | Starling Connect |
|---|---|---|---|---|---|
| Identity Lifecycle Management | ��✓ Full | ✓ Full | ✓ Full | — | Limited (SCIM only) |
| Provisioning/Deprovisioning | ✓ Comprehensive | ✓ Comprehensive | ✓ Comprehensive | — | ✓ SCIM-based |
| Role-Based Access Control | ✓ Advanced hierarchy | ✓ Advanced hierarchy | ✓ Advanced hierarchy | — | — |
| Attestation/Recertification | ✓ Full workflows | ✓ Full workflows | ✓ Full workflows | ✓ For data access | — |
| Segregation of Duties (SoD) | ✓ Detection & enforcement | ✓ Detection & enforcement | ✓ Detection & enforcement | — | — |
| Risk Scoring & Analytics | ✓ Yes | ✓ Yes | ✓ Yes | — | — |
| Self-Service Portal | ✓ Yes | ✓ Yes | ✓ Yes | ✓ Yes (for data) | — |
| Cloud Governance | ✓ Via connectors | ✓ Native | ✓ Native | ✓ SharePoint/OneDrive | Specialized |
| Unstructured Data Focus | — | — | — | ✓ Yes | — |
| SCIM Provisioning | Optional add-on | Optional add-on | Optional add-on | — | ✓ Core function |
| Cloud App Provisioning | Via connectors | Via connectors | Via connectors + Starling | — | ✓ Specialized |
| On-Premises Deployment | ✓ Yes | — | — | ✓ Yes | — |
| Fully Managed SaaS | — | ✓ Yes | ✓ Yes (Modern) | Optional cloud | ✓ Yes |
| Compliance Reporting | ✓ Comprehensive | ✓ Comprehensive | ✓ Comprehensive | ✓ For data access | — |
| 100+ Connectors | ✓ Yes | ✓ Yes | ✓ Yes | Limited | — |
| Power BI Dashboards | ✓ Yes | ✓ Yes | ✓ Yes | ✓ Yes | — |
| Behavior-Driven Governance | ✓ With OneLogin integration | ✓ With OneLogin integration | ✓ With OneLogin integration | — | — |
| Deployment Speed | 6-12 months | 4-8 weeks | 2-4 weeks | Depends on edition | 1-2 weeks |
| Infrastructure Management | Organization responsible | One Identity responsible | One Identity responsible | Organization responsible | One Identity responsible |
Layer 1: IAM
- Authentication: "Who are you?"
- SSO: Single login for all apps
- Basic provisioning: Create/delete access
Layer 2: IGA (Identity Manager)
- Access reviews: "Should they still have this?"
- Compliance: Automated attestations
- SoD enforcement: Prevent fraud combinations
- Risk scoring: Who's at risk?
Layer 3: PAM
- Vault: Secure credential storage
- Elevation: Temporary privileged access
- Monitoring: Record privileged sessions
- Rotation: Auto-rotate secrets
Conclusion
One Identity's IGA portfolio addresses the complete spectrum of identity governance needs across enterprise environments. Organizations select products based on deployment preference (on-premises control vs cloud convenience), infrastructure complexity (legacy systems vs cloud-native), and governance focus (broad identity lifecycle vs. specialized data access).
This platform excels at consolidating fragmented identity tools, automating compliance workflows that consume disproportionate resources, and enabling business-driven governance through dleegation of access decisions. Its extensive connector ecosystem, sophisticated role modeling, and deep compliance automation appeal to highly regulated enterprises and complex organizations seeking to enforce least-privilege security models across hybrid infrastructures.