runZero
runZero - Overview
Assets Asset Discovery
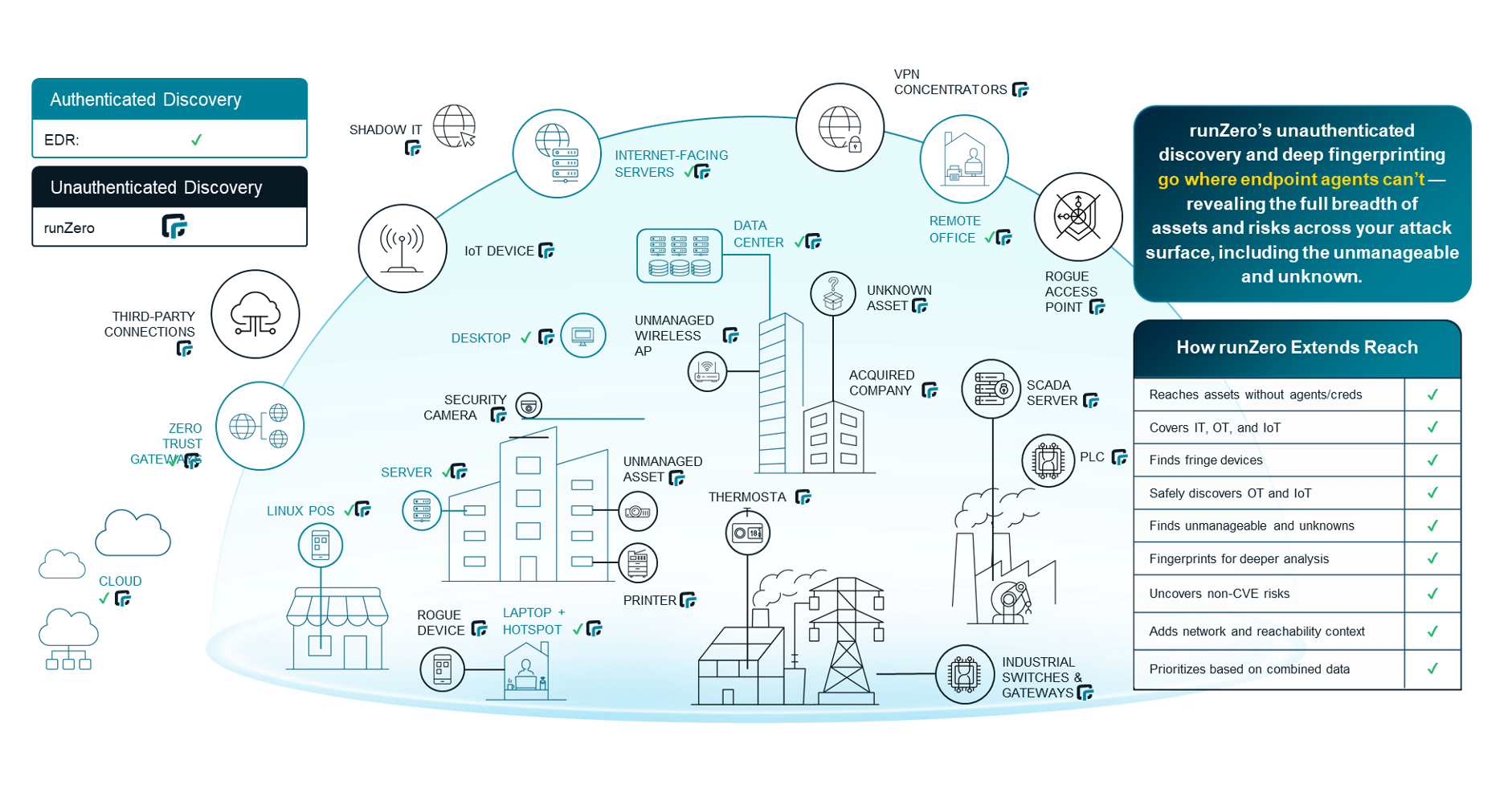
runZero is a modern Cyber Asset Attack Surface Management (CAASM) platform specializing in rapid, comprehensive asset discovery across IT, OT and IoT environments.
Founded in 2018 by HD Moore (creator of Metasploit), runZero pioneered unauthenticated active discovery, the ability to discover and fingerprint network devices without requiring credentials, agents, or network taps. This approach revolutionized asset discovery, by delivering complete inventory visibility in hours instead of weeks or months
- Core Philosophy: "You dan't secure what you don't know you have." runZero's mission is to eliminate asset visibility gaps through intelligent, safe, multimodel discovery that surfaces 25-30% more devices than traditional inventory tools.
- Key Market Position: Gartner Peer Insight's "Customers' Choice" for CAASM; created the modern active discovery market category; recognized for speed, ease of deployment, and comprehensive device fingerprinting.
- Business Model: Cloud SaaS platform with flexible deployment (cloud, on-premises); pricing based on discovery scope (number of assets)
How to position?
Primary Target Customer Segments
Organizations with high velocity IT change
Organizations experiencing rapid growth, frequent M&A activity, cloud migration or digital tranformation face constant infrastructure change that outpaces manual inventory processes. IT teams maintain spreadsheets that become outdated within weeks. Security teams can't assess risk because they don't know what system exist.
Manufacturing & Industrial Operations
Manufacturing environments blend IT and OT, computers, servers, routers alongside industrial equipment, PLCs, sensors, SCADA systems (OT). OT systems are often decades old, fragile and running critical production. Traditional active scanning risks disruption.
runZero's safe, tunable active scanning and robust passive discovery specifically address this: organizations can scan OT environments without disrupting production, discovering equipment IT never knew existed. The NREL/CECA report validates that active discovery is safe in OT environments done correctly.
Healthcare Organizations
Hospitals have medical devices scattered throughout infrastructure: bedside monitors, infusion pumps, diagnostic equipment, patient wearables. IT has no central inventory of these devices. Devices run specialized, often ancient operating systems that can't run security agents.
runZero's agentless discovery finds these devices, classifies them (manufacturer, model, firmware) and flags vulnerabilities
Managed Service Providers and Resellers
Managed Service Providers managing hundreds of customer environments face a critical problem: maintaining accurate asset inventory across customers while scaling efficiently. Manual discovery doesn't scale; expensive appliance-based solutions break the economics.
runZero's cloud-based SaaS model enables MSPs to deploy discovery across customer environments from a single console, automatically discovering assets, flagging shadow IT, and identifying vulnerabilities. Integrations with customer CMDBs (ServiceNow, Solarwinds, etc.) enable automated inventory population.
Vulnerability Management Programs
Organizations running vulnerability scanners (Qualys, Tenable, Rapid7, Nessus) identify thousands of vulnerabilities but are blind to unmanaged devices. Vulnerability scanners can't reach OT equipment, air-gapped systems, devices that block active probes. Patches are prioritized on scanned devices while vulnerabilities on unmanaged devices go invisible.
runZero bridges this gap: it discovers the unmanaged devices; vulnerability management tools then assess them. Together, they close the visibility gap.
Cross-Sell Opportunities
From CMDB/ITSM to Real-Time Inventory
Organizations with ServiceNow, Solarwinds ITSM, JumpCloud Asset Management, or other CMDB systems maintain inventory but face constant staleness. As infrastructure evolves, CMDBs lag behind.
runZero auto-populates and keeps CMDBs current, eliminating manual data entry and ensuring inventory reflects reality.
Message: "Your CMDB is a historical database, not a living inventory. runZero continuously discovers what's actually connected and auto-updates your CMDB. Your inventory becomes current, accurate and reflects your actual infrastructure in real-time.
From Incident Response to Attack Surface Management
Organizations responding to security incidents discovery they don't have complete infrastructure inventory. Post-incident, they need asset discovery to prevent repeat attacks
Example customers
- Organizations Managing Multiple Networks or Geographies Organizations with multiple data centers, office locations, or regional networks struggle to maintain consistent inventory across sites. runZero discovers assets uniformly across all environments, providing unified inventory
- Organizations preparing M&A or divestitures During acquisitions, IT must rapidly inventory the target company's infrastructure to assess integration complexity, identify redundancies, and establish security controls. runZero accelerates this: initial scan in hours provides complete inventory of the acquired company's assets
Kappa Data offers a network and security health-check towards their partners. White-labelled, we do a runZero scan on the end-customer's network together with an interview to offer a gap-analysis and improvement plan. This covers vulnerabilities, end-of-life devices, and general cybersecurity roadmap
Core Features
Active Discovery (Intelligent Network Scanning)
Active discovery is runZero's signature capability. Rather than passive listening, runZero sends benign, standards-conformant network probes and analyzes device responses to identify exactly what's on the network.
 How it works: runZero Explorers (lightweight scanners deployed on-premises or in cloud) send SNMP queries, HTTP requests, and other standard protocols to network addresses. Devices respond with information: "I'm a Windows Server 2019", "I'm an Extreme Networks switch", "I'm a medical monitoring device". From these responses, runZero fingerprints exact device type, manufacturer, model, firmware, and running services.
How it works: runZero Explorers (lightweight scanners deployed on-premises or in cloud) send SNMP queries, HTTP requests, and other standard protocols to network addresses. Devices respond with information: "I'm a Windows Server 2019", "I'm an Extreme Networks switch", "I'm a medical monitoring device". From these responses, runZero fingerprints exact device type, manufacturer, model, firmware, and running services.
 Advantages:
Advantages:
- Complete fingerprinting: Identifies exact device models and firmware versions, not just "Windows Server"
- Fast: Scans complete in hours or days, not weeks
- No credentials needed: Unauthenticated scanning works on unmanaged devices IT doesn't have access to
- Highly configurable: Fine-grained tuning for scan speed, protocol selection, excluded hosts ensures safe operation even in sensitive OT environments
- Safe by design: Only standard, conformant packets; research-driven approach prevents disruption
OT Safety: runZero specifically engineered active discovery to be safe in OT environments. NREL/CECA report validated that active discovery is safe when done correctly. Fine-grained tuning, standards-conformant packets, and extensive protocol handling prevent disruption even on decades-old equipment
Passive Discovery (Continuous Monitoring)
 For environments where active scanning is uncomfortable (air-gapped networks, extremely fragile OT, high-security facilities), runZero provides passive discovery that continuously listens to network traffic without sending probes
For environments where active scanning is uncomfortable (air-gapped networks, extremely fragile OT, high-security facilities), runZero provides passive discovery that continuously listens to network traffic without sending probes
How it Works: runZero observes network traffic (via mirror/SPAN port or log imports) and learns about devices from their communications. When a device sends DHCP requests, HTTP traffic, or proprietary protocol communications, runZero observes and fingerprints it.
Advantages:
- Non-intrusive: Zero risk of disruption
- Continuous: Always-on monitoring provides ongoing visibility
- Safe for fragile systems: No probes sent
- Works on air-gapped networks: If traffic can be captured and imported
Limitation: Slower than active discovery; only identifies devices that communicate during observation window
Fingerprinting (Exact Device Identification)
Fingerprinting is how runZero identifies "Canon imagePRUNER 4000 running firmware 5.2.1" without contacting Canon. Every device communication in characteristic ways; runZero recognizes these patterns
- How it works: When runZero analyzes device responses, it builds a fingerprint (a unique signature of behavior patterns, response formats, and metadata). runZero compares this fingerprint to a database of millions of known devices, identifying exact device type, model, firmware and configuration
- Accuracy: 99%+ identification accuracy for common devices; reduces false positives in vulnerability assessment by correctly identifying device types
- Value: Accurate fingerprinting enables precise vulnerability mapping. Critical vulnerabilities affecting specific device models are flagged; false alarms on misidentified devices are eliminated
Vulnerability Detection in Discovery
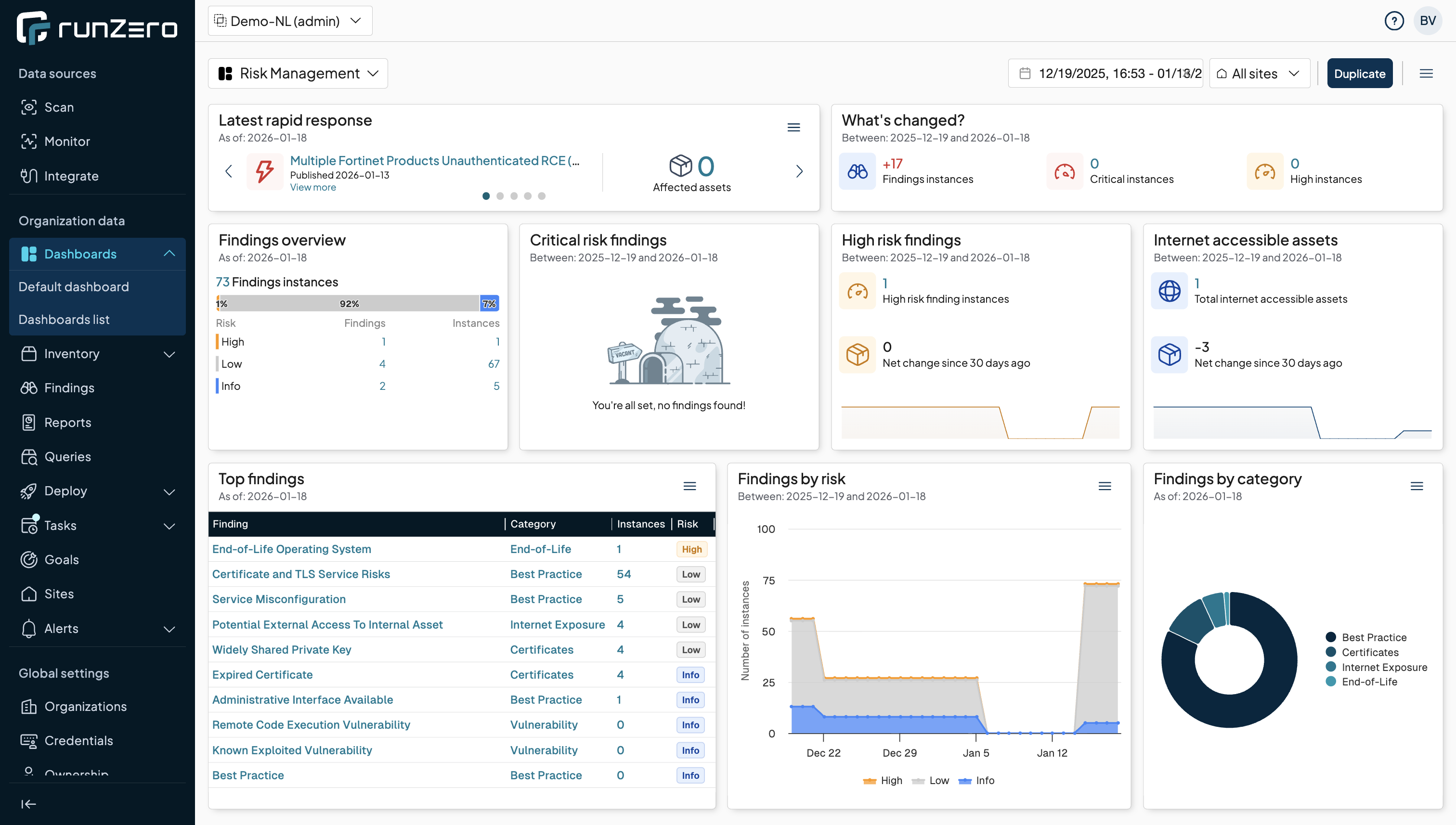
Modern runZero (integrated with Nuclei vulnerability scanner) doesn't just discover devices, it immediately assesses them for known vulnerabilities
How it works: When runZero discovers a device as "Windows Server 2016 with outdated patch level," it checks: "Is this configuration vulnerable to known CVEs?" Flags high-risk configurations (outdated OS, weak protocols, exposed services)
Integration: runZero feeds vulnerability data into vulnerability management platforms, SIEM and XDR tools for centralized risk assessment.
API Integrations

runZero integrates with dozens of platforms to provide comprehensive inventory by unifying data from multiple cloud sources
- Cloud Providers: AWS, Azure, Google Cloud
- Identity Platforms: Active Directory, Entra ID
- IT Management: ServiceNow, Netbox, Atlassian
- Vulnerability Management: Qualys, Tenable, Rapid7
- EDR/MDR: CrowdStrike, Microsoft Defender, SentinelOne
- Network: Palo Alto, VMWare
- Threat Intelligence: Shodan, Censys
Advantage: runZero becomes the central clearinghouse for asset data. It discovers assets through active/passive scanning, enriching with data from other platforms, feeding consolidated inventory to downstream systems
External Attack Surface Management
runZero can scan external IP space (public-facing infrastructure) to identify exposed services, misconfigured firewalls, and shadow IT exposed to internet
How it works: Configure ASN numbers or domain names; runZero scans external-facing IP addresses to identify web servers, management interfaces, or other exposed infrastructure
Use case: Discover accidentally exposed cloud buckets, development servers exposed to internet, or rogue DNS entries pointing to attacker infrastructure.
Network Topology and Visualization
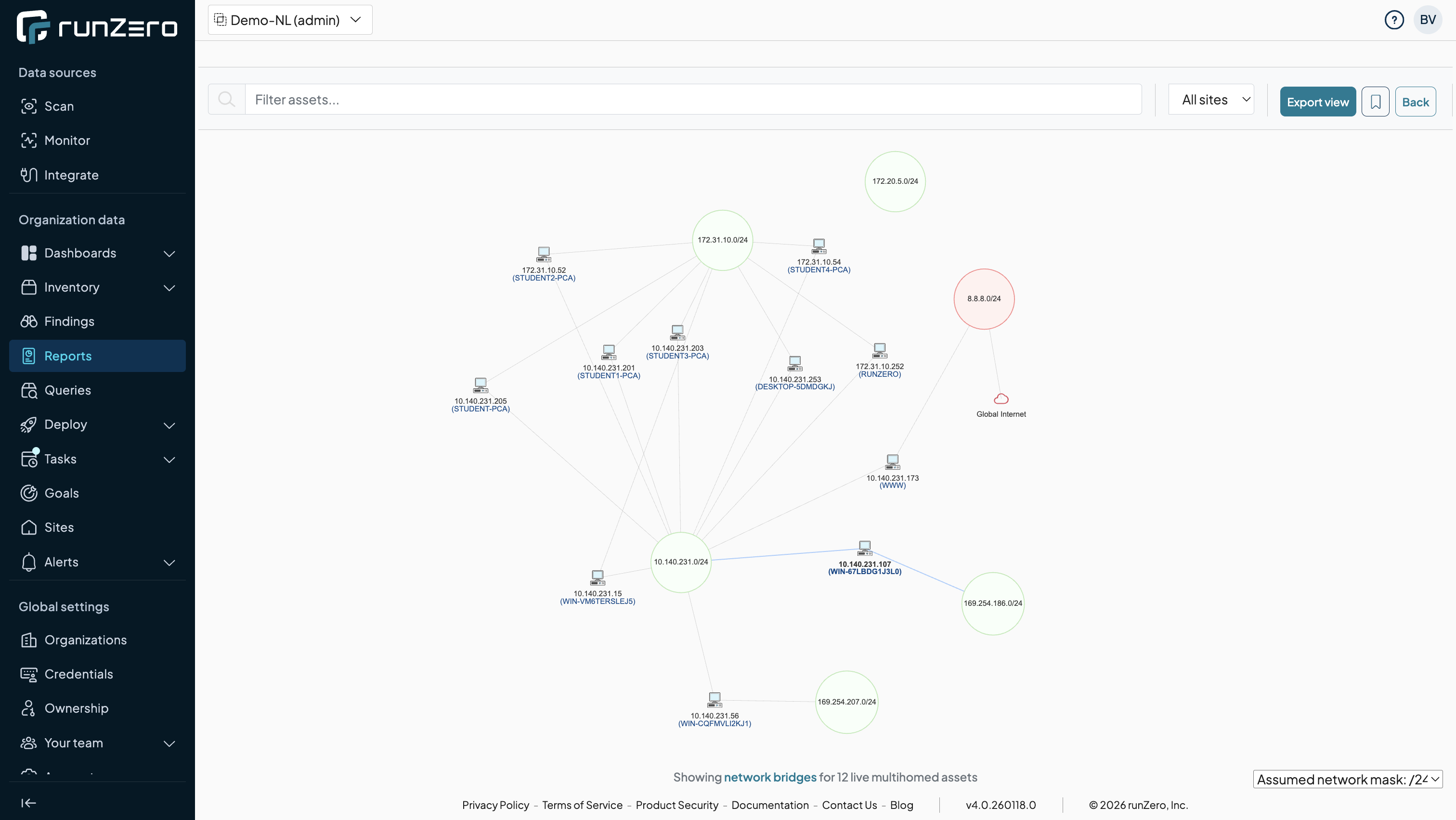 runZero generates network diagrams showing device relationships, network segmentation, and topology. Identifies network bridges (devices with multiple network interfaces) that could violate network segmentation
runZero generates network diagrams showing device relationships, network segmentation, and topology. Identifies network bridges (devices with multiple network interfaces) that could violate network segmentation
Business Value: Quick visualization reveals architecture issues, excessive network bridges, poor segmentation, unintended network connectivity.
Feature overview
Deployment Models
- Cloud SaaS: Explorers deployed on-premises or in cloud environments; all data processing, storage, and analytics in runZero cloud. Ideal for organizations wanting minimal on-premises infrastructure
- On-Premises: Full deployment on customer's own infrastructure; supports air-gapped environments
Scalability
runZero scales from single-site deployments to multinational enterprises with hundreds of sites:
- Single Explorer scans local network
- Multiple explorers coordinate scans across distributed networks
- Central management console aggregates inventory from all sites
Audit and Compliance
runZero maintains detailed change logs:
- When was each device discovered?
- When did configuration change?
- When were vulnerabilities flagged?
- When was remediation completed?
- Who authorized changes?
This audit rail satisfies compliance requirements demonstrating continuous asset monitoring and vulnerability management.
runZero vs Armis: Realistic Comparison
Both runZero and Armis address identity and asset visibility with fundamentally different approaches
Where runZero excels
- Speed of initial deployment: runZero achieves complete inventory in hours; Armis requires days or weeks of behavioral learning
- Discovery without credentials: Active scanning works on unmanaged, IoT, OT devices without requiring authentication
- Active scanning precision: Active fingerprinting identifies exact device models, firmware versions, and services running
- External attack surface: runZero can scan external IP space to identify exposed infrastructure; Armis focuses on internal networks